Table of Contents
ToggleComplete Guide to Protecting Digital Content from Unauthorized Access. Comprehensive Strategies for Preventing Credential Sharing in Online Education and Video Streaming Platforms. By Inkrypt Videos Security Team. Protecting Premium Educational Content Through Advanced DRM Technology
The Growing Threat to Digital Content
Student credential sharing has emerged as one of the most significant challenges facing online course creators and video streaming platforms in 2025. With the global e-learning market reaching $366 billion and serving over 1.1 billion users worldwide, protecting premium educational content from unauthorized access has become essential for sustainable business operations.
Recent industry analysis reveals that content creators lose 15-30% of potential revenue annually due to credential sharing, while digital piracy costs the U.S. economy $29.2 billion per year. For course creators and video platforms that have invested countless hours developing high-quality content, implementing comprehensive security measures isn’t optional—it’s a business imperative.
This guide provides actionable strategies to prevent unauthorized access while maintaining optimal user experiences for legitimate subscribers.
Understanding Credential Sharing and Unauthorized Access
What Is Credential Sharing?
Credential sharing occurs when enrolled users provide their login credentials to unauthorized individuals, allowing them to access paid content without enrollment or payment. This practice represents digital piracy that directly impacts creator revenue and violates terms of service agreements.
Common Sharing Scenarios
- Family and Friend Networks: Users frequently share access with family members or close friends interested in similar content but unwilling to pay subscription fees.
- Study Groups: Academic environments foster collaboration that can inadvertently lead to unauthorized sharing when groups decide to split course costs.
- Commercial Reselling: More serious cases involve individuals creating businesses around purchasing premium content and reselling access through shared accounts.
Financial Impact on Content Creators
Content creators report that credential sharing can reduce potential revenue by 15-30% annually. Consider a typical scenario: a premium course priced at $297 with 1,000 enrolled students. If just 20% of students share credentials with one additional person, the creator loses approximately $59,400 in potential revenue.
Beyond direct revenue loss, credential sharing creates additional costs, including infrastructure burden from unauthorized users consuming bandwidth and server resources, diluted learning experiences, and compromised community value when private forums are populated by non-paying participants.
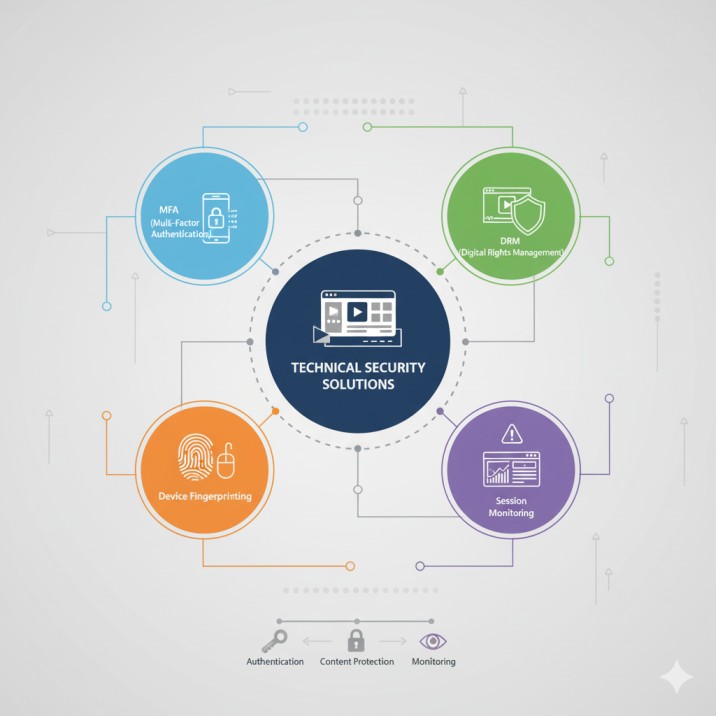
Essential Technical Security Solutions
1. Single Session Enforcement
Modern Learning Management Systems and video hosting platforms support single sign-on features that allow only one active session per account. When a new login occurs, previous sessions are automatically terminated. This immediately prevents simultaneous access from multiple devices and provides a clear deterrent without compromising user experience.
2. Multi-Factor Authentication (MFA)
Two-factor authentication adds essential security layers by requiring additional verification beyond username and password combinations. Effective MFA methods include SMS verification codes, authenticator apps like Google Authenticator, and email authentication links. Organizations implementing 2FA report significant reductions in unauthorized access attempts.
3. Device Fingerprinting and Behavioral Analysis
Advanced platforms utilize device fingerprinting technology to identify unique characteristics of accessing devices, creating digital signatures that detect unusual access patterns. Key elements include browser configuration, screen resolution, IP address data, and operating system details. This sophisticated protection enables platforms to flag suspicious login attempts and build trust scores for recognized devices.
4. Geographic and Time-Based Controls
Monitoring IP patterns provides insights into potential credential sharing while enabling location-based access controls. Sudden IP changes across different countries can indicate sharing, triggering additional authentication requirements. Implementing session duration limits and scheduled access windows adds protection while accommodating legitimate learning schedules.
Advanced Content Protection with DRM Technology
Digital Rights Management (DRM) technology provides the most comprehensive protection by encrypting content and controlling access, downloading, and sharing capabilities. Modern DRM solutions offer content encryption during transmission and storage, license management that controls access duration and device limits, and dynamic watermarking with unique identifiers embedded in content to trace unauthorized distribution.
Professional hosting platforms designed for educational content provide security features, including signed URLs with temporary, encrypted links that expire automatically, domain restrictions ensuring videos play only on authorized websites, and real-time analytics with detailed viewing data to identify unusual access patterns.
Monitoring and Detection Methods
Modern platforms generate extensive data revealing credential-sharing patterns when properly analyzed. Key monitoring metrics include login frequency patterns that deviate from normal learning behavior, geographic inconsistencies such as rapid location changes, device usage analysis showing multiple device types accessing single accounts, and engagement patterns revealing multiple distinct learning styles within single accounts.
Real-time monitoring systems can detect and respond to credential sharing attempts as they occur through live session tracking, instant alerts when suspicious activity is detected, and adaptive responses that automatically increase security requirements when threats are identified.
Implementation Roadmap for Content Creators
Phase 1: Immediate Actions (0-30 days)
- Implement single session enforcement across all user accounts • Revise terms of service to explicitly prohibit credential sharing • Configure basic monitoring for suspicious access patterns • Communicate security policies clearly to existing users.
Phase 2: Enhanced Protection (1-3 months)
- Deploy two-factor authentication across all accounts • Set up device fingerprinting and geographic tracking • Implement platform-specific security plugins and tools • Develop a comprehensive legal framework for enforcement.
Phase 3: Advanced Security (3-6 months)
- Deploy comprehensive DRM protection with watermarking • Develop specialized monitoring and detection systems • Create exclusive value propositions that cannot be easily shared • Implement regular security audits and optimization procedures.
Citations and Key Resources
The following resources and studies were instrumental in developing this comprehensive guide on online course security and credential sharing prevention.
Academic and Industry Research
1. K-12 Cybersecurity Research (2025) CIS MS-ISAC 2025 K-12 Cybersecurity Report: Where Education Meets Community Resilience. Available at: https://www.cisecurity.org/insights/white-papers/2025-k12-cybersecurity-report
This comprehensive report analyzed over 5,000 K-12 organizations between July 2023 and December 2024, revealing that 82% of reporting schools experienced cyber threat impacts. The study provides critical insights into educational cybersecurity challenges and the 14,000 security events recorded during the reporting period, highlighting the urgent need for robust security measures in educational institutions.
2. Global Digital Piracy Impact Study (2025) U.S. Chamber of Commerce Global Innovation Policy Center – Impacts of Digital Piracy on the U.S. Economy. Available at: https://www.uschamber.com/technology/data-privacy/impacts-of-digital-piracy-on-the-u-s-economy
This economic analysis estimates that global online piracy costs the U.S. economy at least $29.2 billion in lost revenue each year. The study uses macroeconomic modeling to demonstrate how digital video piracy results in significant losses across content production firms and technology companies, providing crucial context for understanding the financial impact of educational content theft.
Industry Standards and Compliance
3. Educational Privacy and Security Guidelines U.S. Department of Education Student Privacy Policy Office Available at: https://studentprivacy.ed.gov/
Comprehensive guidance on protecting student privacy while using online educational services, including FERPA compliance requirements and best practices for educational technology implementation. These resources provide the legal and regulatory framework for implementing security measures in educational contexts.
4. Cybersecurity Investment Analysis Cybersecurity Ventures – Global Security Market Trends Available at: https://cybersecurityventures.com/
Industry analysis showing global cybersecurity spending reaching $1.75 trillion cumulatively from 2021-2025, highlighting the increasing investment in security technologies across all sectors, including education. This data supports the business case for investing in comprehensive course protection measures.
Conclusion
Preventing unauthorized access requires a multi-layered approach combining technical solutions, legal frameworks, and ongoing monitoring. As the online education industry continues its explosive growth—projected to reach $844 billion by 2030—comprehensive security measures become essential for sustainable business operations.
Content creators who invest in robust protection not only safeguard immediate revenue but also preserve long-term value and exclusivity. The most effective strategies combine multiple prevention methods: technical measures like MFA and session management provide baseline protection, while DRM systems and secure hosting offer advanced content security.
Remember that perfect security matters less than creating sufficient friction to discourage unauthorized access while maintaining positive experiences for legitimate users. By implementing these proven strategies, content creators can protect their valuable digital assets while continuing to serve committed learners effectively.
For content creators serious about protecting their intellectual property, comprehensive security investment pays dividends through preserved revenue, maintained content value, and the ability to continue producing high-quality educational experiences.
Ready to protect your digital content? Inkrypt Videos offers advanced DRM encryption, secure video hosting, and comprehensive content protection solutions. Visit inkryptvideos.com to learn how our cloud video platform can safeguard your valuable content from unauthorized access and piracy.
FAQs
Student credential sharing occurs when learners provide their login details to unauthorized users, allowing multiple people to access paid course content with one account. This practice violates terms of service and causes revenue loss for course creators.
Multi-factor authentication (MFA) requires users to verify identity through a secondary method like SMS codes or authentication apps before accessing courses. This makes credential sharing significantly harder since unauthorized users need both password and authentication access.
Device limits restrict how many devices can simultaneously access one account, discouraging widespread credential sharing. This approach balances security with legitimate user needs, such as accessing courses from laptops and mobile devices.
Social login requires authentication through Facebook, Google, or LinkedIn accounts that students typically won’t share with others. This method reduces password sharing while simplifying the login experience for legitimate users.
Parallel login restriction prevents multiple users from accessing the same account simultaneously from different devices or IP addresses. While not foolproof, it deters real-time credential sharing during live sessions or time-sensitive courses.
Device fingerprinting identifies unique device characteristics to track and limit which devices can access an account. This technology helps platforms detect when credentials are being used across unauthorized devices beyond permitted limits.
No. While 2FA adds security layers, determined users can still share authentication codes or forward verification emails. It serves as a deterrent rather than an absolute prevention method.
Course creators may terminate access, suspend accounts, or revoke certificates when detecting shared credentials. Educational platforms often include anti-sharing clauses in terms of service, making violations grounds for permanent bans.
Yes, platforms monitor login patterns including IP addresses, device information, geographic locations, and session activity to identify suspicious credential sharing behavior. Advanced systems use WP Activity Log or similar tools to view all user actions.
Certificates issued only to verified account holders discourage sharing since unauthorized users cannot receive accredited credentials in their names. Name changes on certificates are typically restricted or monitored to prevent fraud.
Sharing credentials violates intellectual property rights and terms of service agreements, potentially resulting in account termination and loss of paid access. Some platforms pursue legal action for significant piracy or content theft cases.
Single sign-on allows only one active user session at a time, automatically logging out previous sessions when new logins occur. This feature prevents simultaneous access while maintaining convenience for legitimate individual users.