Table of Contents
ToggleProtecting educational content is more critical than ever—discover how Digital Rights Management (DRM) empowers educators to secure, control, and share learning materials with confidence.
Key Takeaways
Educational DRM secures digital teaching assets like textbooks, lectures, and curricula from unauthorized sharing, preserving revenue and academic integrity.
Start with a DRM needs audit to assess content sensitivity, piracy risk, compliance requirements, and ROI before selecting a solution.
Choose DRM tools compatible with major LMS platforms and all student devices while ensuring strong encryption and user-friendly access.
Integrate DRM into content workflows with permissions like view-only, print limits, and expiration dates to automate protection.
Balance protection with usability by enabling text-to-speech, annotation, and offline access to avoid hindering learning outcomes.
Use forensic watermarking to trace and deter content leaks, especially for high-stakes materials like certification exams.
Transparent communication and user-centric design (e.g., SSO, multi-device access) improve adoption and reduce support issues.
Ongoing monitoring and legal vigilance help adapt DRM strategies to new threats and changing accessibility or copyright laws.
A well-executed DRM strategy future-proofs digital education, enabling scalable, secure, and accessible learning experiences for all stakeholder
Introduction to DRM for Educational Content Protection
As e-learning materials become increasingly digital, safeguarding academic intellectual property is critical. Educational DRM (Digital Rights Management) technology empowers creators and institutions to control how digital content is accessed, copied, and shared after distribution. This guide explores practical DRM implementation strategies for course materials, textbooks, and training resources, ensuring educators and publishers retain authority over their valuable digital assets.
Understanding DRM's Role in Education
Digital Rights Management (DRM) uses access control technologies to protect proprietary educational content and systems. For educators and institutions, academic DRM solutions actively prevent unauthorized sharing of:
Teaching materials
E-textbooks
Lecture videos
Digital curricula
This e-learning content protection enables creators and publishers to:
Generate fair revenue from their investments.
Maintain precise control over how resources are distributed and used.
By securing digital assets, DRM sustains a trustworthy educational ecosystem.
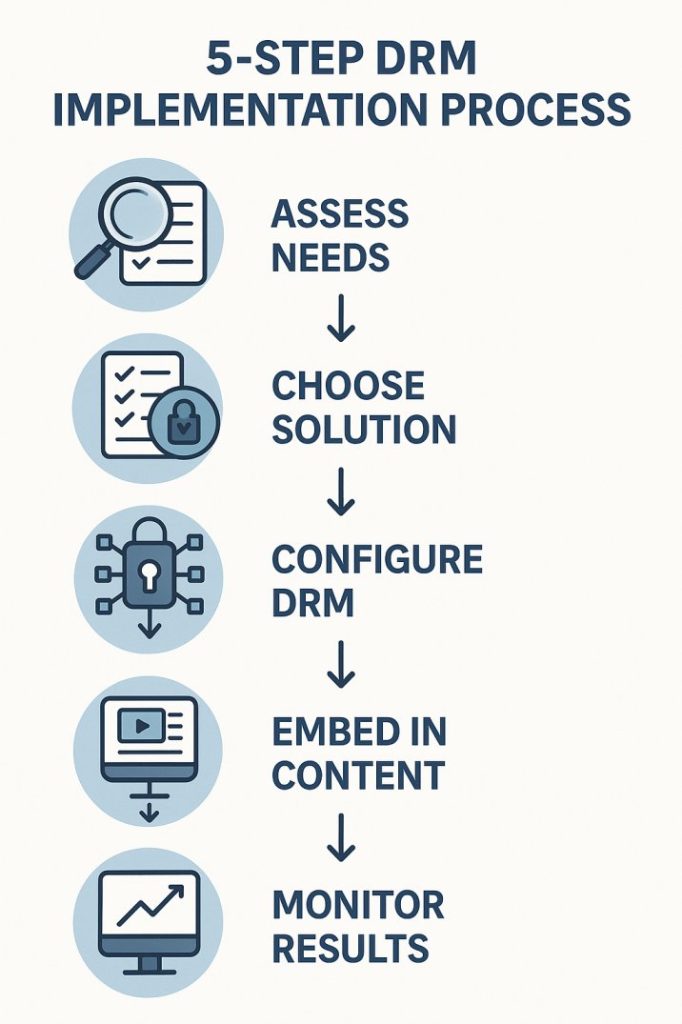
Step-by-Step Guide to Implementing DRM in Education
Deploying DRM for educational materials requires strategic planning to balance security and learning accessibility. Follow these key phases:
Step 1: Assess Your DRM Needs
Audit Content Sensitivity:
Identify materials needing protection (e.g., proprietary curricula, premium video lectures).Evaluate Piracy Risks:
Analyze potential revenue/credibility loss from unauthorized sharing.Consult Legal Experts:
Verify copyright compliance requirements for your region and content type.Calculate ROI:
Compare DRM implementation costs vs. projected piracy losses.
Step 2: Select the Right DRM Solution
Platform Compatibility:
Ensure support for all student devices (iOS/Android/Chromebooks).LMS Integration:
Prioritize solutions compatible with Moodle, Canvas, or Blackboard.Security & Support:
Choose vendors offering encryption + 24/7 technical assistance.User Experience:
Test demo versions for accessibility (e.g., screen reader support).
Step 3: Implement & Configure DRM
Procure licenses from reputable DRM providers (e.g., Adobe, Vitrium).
Integrate with your content management system (CMS).
Conduct cross-platform testing (web/mobile/offline access).
Train administrators and content creators on DRM workflows.
Step 4: Embed DRM in Content Creation
Modify Workflows:
Automate the DRM application during content export/upload.Enable Dynamic Updates:
Ensure new editions/updates inherit protection settings.Set Usage Rules:
Configure permissions (view-only, print limits, expiry dates).
Step 5: Monitor & Optimize
Track Effectiveness:
Use analytics to detect breach attempts or access issues.Update Proactively:
Patch vulnerabilities and adapt to new threat vectors.Gather User Feedback:
Survey students/instructors about access barriers.Maintain UX Balance:
Adjust restrictions if they impede legitimate learning.
Unique DRM Challenges for Professional Associations
Professional associations confront specialized content protection hurdles when securing high-value resources like certification programs and industry standards. Unlike traditional publishers, they must:
Shield proprietary accreditation materials and compliance documents
Manage tiered access across diverse stakeholders
Combat credential fraud and standards piracy threatening institutional credibility
Critical Challenges & Solutions:
A. Multi-Tier Membership Complexity
Problem: Varying access needs for students, practitioners, and corporate partners.
Solution: Implement granular role-based DRM controls that automatically adjust permissions by membership tier.
B. Credential Fraud Risks
Problem: Exam content leaks devalue certifications.
Solution: Combine dynamic watermarking with test lockdown browsers during high-stakes assessments.
C. Standards Piracy Vulnerability
Problem: Illicit resale of premium industry manuals ($500+).
Solution: Enforce print/export restrictions + explore blockchain verification for document authenticity.
D. Cross-Platform Access Demands
Problem: Members use field tablets, conference laptops, and office desktops.
Solution: Deploy HTML5-based DRM compatible with Android/iOS/Windows ecosystems.
Real-World Applications:
Engineering Associations: Protecting ASME/ISO standards from redistribution
Medical Boards: Securing CME modules against credential sharing
Certification Bodies (e.g., PMI): Preventing exam question leaks to “dump sites”
Integrating DRM with Your Association’s LMS
Securing educational content within your Learning Management System (LMS) requires specialized DRM implementation steps. This layered approach ensures only authorized members access premium resources like certifications and standards.
Step-by-Step Integration Process
Audit Protected Content
Identify high-value materials needing security (certification exams, standards PDFs) and assign risk-based protection tiers.Select LMS-Compatible DRM
Choose solutions with proven integration for:Moodle (via LTI 1.3)
Canvas (API plugins)
Blackboard (Building Block support)
Prioritize solutions offering SCORM/xAPI tracking.
Implement Granular Access Controls
Configure role-based permissions:plaintextStudents → View-only access Professionals → Download + print (watermarked) Partners → Full redistribution rights
Deploy Frictionless Authentication
Integrate SAML/SSO with membership databases
Require multi-factor authentication for sensitive resources
Conduct Real-Environment Testing
Verify functionality across:Mobile (iOS/Android training apps)
Offline access for field professionals
Legacy browsers used by corporate members
Proactive Maintenance & Troubleshooting
- Prevent Compatibility Issues: Schedule quarterly DRM-LMS compatibility checks during LMS updates
- Member Support: Create video guides for common access scenarios (e.g., “Solving Playback Errors on iPads”)
- Security Updates: Establish automated alerts for DRM vulnerability patches
- Usage Analytics: Monitor heatmaps to detect UX friction points (e.g., drop-offs at authentication steps)
Understanding DRM Limitations in Education
While essential for protecting academic content, DRM has inherent constraints requiring careful management:
Potential Learning Disruption:
Overly strict DRM can hinder legitimate educational activities like content annotation or accessibility adjustments, impacting teaching effectiveness.
Mitigation: Implement tiered access permissions for educators vs. students.Security Vulnerability:
Tech-savvy users may bypass DRM protections, creating content leakage risks.
Mitigation: Combine encryption with forensic watermarking to trace leaks.Increased Operational Costs:
DRM implementation adds expenses for licensing, integration, and maintenance.
Mitigation: Calculate ROI against piracy losses; explore open-source DRM options.Compatibility Challenges:
Not all DRM systems work seamlessly across older devices or specialized learning tools.
Mitigation: Prioritize cross-platform solutions; provide alternative access paths.
DRM Best Practices for Education: Balancing Security & Learning
Implement these strategies to maximize protection while minimizing educational disruption:
Prioritize Pedagogical Accessibility
→ Design flexible DRM policies that allow:Content annotation for active learning
Text-to-speech functionality
Limited offline access for low-connectivity areas
Goal: Never let security override core learning objectives.
Transparent Stakeholder Communication
→ Explain DRM’s purpose through:Student onboarding materials (“Protecting your course investment”)
Faculty training sessions
Public copyright compliance statements
Impact: Builds trust while reducing support queries.
Proactive Legal Vigilance
→ Monitor regulatory shifts in:Digital fair use provisions
Accessibility compliance (WCAG 2.2)
International copyright treaties
Action: Conduct quarterly policy reviews with legal counsel.
User-Centric Design Principles
→ Minimize learning friction by:Implementing single sign-on (SSO) integration
Allowing 3-5 authorized devices per user
Providing clear error resolution guides
Forensic Watermarking: Trace & Deter Content Leaks
For associations battling credential piracy and standards theft, forensic watermarking is your invisible security ally. This technology embeds unique identifiers in digital content to trace leaks back to specific users or devices.
How Educational Watermarking Works
Personalized Marking
→ Each member receives content with hidden identifiers (e.g., “UserID-ACME2025-DeviceMAC”)
→ Visible watermarks display the user email for psychological deterrenceLeak Investigation
→ Scan piracy sites/dark web for watermarked materials
→ Extract identifiers to pinpoint source accountsEnforcement Actions
→ Terminate violating memberships
→ Initiate DMCA takedowns with watermark evidence
→ Pursue legal claims for high-value leaks (e.g., stolen certification exams)
Best Practices for Associations
A. Multi-Layered Marking
Visible: Display user email on certification PDFs
Invisible: Embed forensic codes in video/audio streams
B. Proactive Deterrence
“All materials contain traceable watermarks. Unauthorized sharing = membership termination.”
Include in membership agreements and content access warnings
C. Integrated Security
Combine with DRM to:
Prevent bulk downloads (technical barrier)
Trace leaked copies (forensic backup)
Case Study: CFA Exam Protection
The Chartered Financial Analyst program:
Embeds candidate-specific codes in practice exams
Shut down 12 dump sites in 2023 using watermark evidence
Reduced leaks by 78% with visible/invisible dual marking
Implementation Checklist
Audit high-risk content (exams/standards)
Select watermarking solution (e.g., Verimatrix, ARG)
Configure user-specific identifier templates
Update membership agreements with watermark clauses
Train staff on leak investigation workflows
Conclusion: DRM as a Catalyst for Secure Digital Learning
Implementing effective educational DRM demands strategic planning and continuous refinement. By embracing purpose-built protection solutions that prioritize both security and accessibility, institutions and creators can:
Safeguard intellectual property while maintaining content quality
Enable new learning models (personalized, remote, OER-integrated)
Build sustainable digital ecosystems where innovation thrives
The Future-Ready Approach:
Forward-thinking DRM transcends mere content locking – it becomes the foundation for trusted, scalable digital education. When balanced correctly, these technologies:
Empower creators to invest in better resources
Ensure institutions comply with evolving regulations
Deliver frictionless experiences for all learners
Experience Next-Gen Academic DRM
At Inkrypt Videos, we engineer pedagogically aligned DRM solutions specifically for education. Our platform eliminates traditional tradeoffs through:
- Granular permission controls without accessibility compromises
- LMS-native integration (Canvas, Moodle, Blackboard)
- Automated compliance with WCAG 2.2 and FERPA standards
Educational DRM isn’t just about locking content—it’s about enabling secure, scalable, and accessible digital learning. When thoughtfully implemented, it protects intellectual property while supporting student success.
Ready to protect your digital course materials?
Start your free 30-day trial with Inkrypt Videos today—no payment required, just powerful, educator-focused DRM.
FAQs
DRM, or Digital Rights Management, protects educational content from unauthorized sharing, helping associations control access and maintain the value of their resources
DRM restricts who can view, copy, or share digital materials, making it harder for unauthorized users to distribute or misuse content
Only authorized members or users with valid permissions can access DRM-protected content, ensuring compliance with licensing and privacy rules
DRM secures e-books, training videos, standards documents, certifications, and other digital learning resources commonly used by associations
Associations should choose DRM solutions that offer easy access for legitimate users while still enforcing strong content protection
Access problems often result from device compatibility, browser settings, or strict DRM controls. Clear instructions and support can help resolve these issues
Some DRM systems use watermarking to trace leaks back to specific users, helping associations identify and address breaches quickly
Assess content types, member needs, and platform compatibility before selecting a DRM tool tailored for educational organizations.
Yes, many DRM solutions integrate with popular LMS platforms through plugins or APIs for seamless content protection
Common challenges include balancing security with usability, ensuring device compatibility, and managing user permissions.
DRM helps associations meet copyright, licensing, and privacy requirements by controlling access and tracking content usage


