Table of Contents
Toggle
Introduction: The Silent War Against Video Piracy
Digital video piracy costs the global media and entertainment industry approximately $75 billion annually, with projections showing this could escalate to $125 billion by 2028. Today’s pirates aren’t just operating from shady websites—they’re often authorized users, partners, or even reviewers leaking premium content within minutes of release. Traditional security measures like DRM encryption and access controls can only do so much. Once content gets past these defenses, tracking down the source becomes nearly impossible.
That’s where forensic video analysis steps in, armed with one of its most powerful weapons: dynamic watermarks.
Unlike visible watermarks that can be cropped out or static marks that offer limited information, dynamic watermarks create unique digital fingerprints for every viewing session. These invisible markers silently travel with your content wherever it goes, surviving compression, screen recording, and even analog-to-digital conversion. When pirated content surfaces on torrent sites or streaming platforms, forensic analysis can extract these watermarks and trace the leak back to its exact source.
This technology has become essential for content creators who’ve invested thousands or millions into their work. From online course creators protecting premium educational content to Hollywood studios guarding pre-release screeners, forensic video analysis with dynamic watermarking provides accountability in an increasingly difficult-to-control digital landscape.
What Is Forensic Video Analysis?
Forensic video analysis represents the scientific examination, comparison, and evaluation of video content in legal and investigative matters. This field combines advanced digital forensics, computer vision, and cryptographic techniques to extract hidden information from video files.
At its core, forensic video analysis serves multiple purposes. It verifies the authenticity of video evidence, identifies tampering or manipulation, enhances poor-quality footage for investigation, and, most critically for content protection, traces the origin of leaked or pirated content.
The Evolution of Digital Forensics
Digital watermarking made its first appearance in 1993, but it wasn’t until 2007 that session-based forensic video watermarks emerged. These early systems generated viewer information from cable subscribers’ set-top boxes, marking the beginning of modern content protection.
By 2025, forensic video analysis will have evolved into a sophisticated discipline. Advanced techniques now include frame-by-frame analysis, video stabilization, metadata examination, motion tracking, and most importantly, imperceptible watermark detection. The digital watermarking market, valued at $1.45 billion in 2024, is projected to reach $3.80 billion by 2033, with an annual growth rate of 11.4%. The broader forensic video watermarking solution market is estimated at $1.5 billion in 2025 and projected to grow at a 15% CAGR to approximately $5 billion by 2033.
Why Forensic Analysis Matters
The numbers tell a compelling story. Digital video piracy accounted for nearly 60% of all digital intellectual property theft in recent years. In 2024, piracy sites worldwide received over 229 billion visits. For content creators, these aren’t just statistics—they represent lost revenue, damaged brand reputation, and competitive disadvantages.
Forensic video analysis addresses these challenges by providing traceability and accountability. When a leak occurs, content owners can identify not just that piracy happened, but exactly who was responsible and how the content escaped their control.
Understanding Dynamic Watermarks
Dynamic watermarks represent a significant advancement over traditional watermarking technology. While static watermarks remain the same across all copies of content, dynamic watermarks change based on specific factors like the viewer, session, or playback context.
What Makes Watermarks “Dynamic”?
A dynamic watermark incorporates viewer-specific information that creates a unique identifier for each playback session. This typically includes the user’s email address, IP address, device ID, viewing timestamp, and session ID. The watermark adjusts its position, pattern, or encoding with each viewing, making it extraordinarily difficult for pirates to remove.
Consider this scenario: Two users watch the same online course. User A receives video segments with a watermark pattern AABABBAB, while User B gets BBABAABB. If either user records and uploads the content, forensic analysis can match the exact pattern to identify the leaker.
The Science Behind Invisibility
Dynamic watermarks achieve their effectiveness through sophisticated embedding techniques that maintain imperceptibility. These marks are embedded directly into the video’s pixel data, modifying specific frequency components that human eyes cannot detect. The watermark survives common piracy techniques, including re-encoding, compression, aspect ratio changes, cropping and filtering, and even screen recording or camcording.
The financial impact is staggering. Illegal streaming and downloading cost the US economy between $29.2 billion and $71 billion annually in lost revenue. When including illegal sports streaming, the total reaches an estimated $229 billion. Research has shown that properly implemented forensic watermarks can withstand aggressive tampering attempts. When pirates attempt to remove dynamic watermarks, they face a daunting task. First, they must identify the watermark’s position in each scene, which changes constantly. Second, even if they manage to remove marks from some frames, the process creates visible artifacts throughout the video, making the pirated copy obviously degraded.
How Forensic Watermarking Works
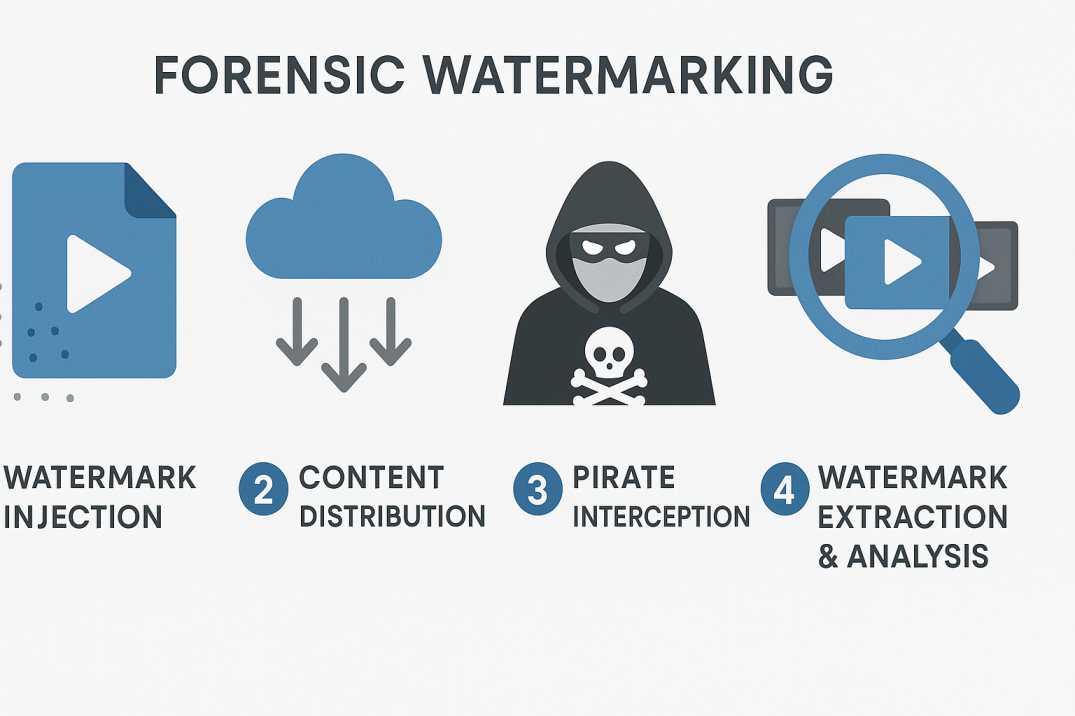
The forensic watermarking process operates through four distinct stages, each critical to catching pirates and protecting content.
Stage 1: Watermark Injection
The process begins with embedding a unique digital fingerprint into the video content. This happens through either server-side embedding (before content reaches the viewer) or client-side embedding (applied on the viewer’s device during playback).
For server-side watermarking, the system integrates the watermark during the video’s encoding stage, creating unique versions or segments for each user. This method provides maximum security but requires more processing power and storage. Client-side watermarking applies marks during playback on the consumer’s device, making it faster but potentially less secure since the watermarking logic exists on the client side.
Stage 2: Content Distribution
Once watermarked, the content travels through its intended distribution channels. The beauty of forensic watermarking lies in its persistence—the mark remains embedded whether the content is streamed, downloaded, shared via email, or even recorded with another camera pointed at the screen.
Each watermark contains metadata that survives the journey. This information might include the original recipient’s account details, the specific date and time of access, the geographic location of playback, and the device or platform used for viewing.
Stage 3: Pirate Interception
If a pirate intercepts and redistributes the content, they typically attempt various manipulation techniques to avoid detection. They might re-encode the video to different formats or resolutions, compress the file to reduce size, apply filters or effects to obscure the watermark, or combine segments from multiple sources to create a “clean” copy.
However, robust forensic watermarks are designed to resist these attacks. The watermark’s data remains recoverable even after significant degradation or tampering.
Stage 4: Watermark Extraction and Analysis
When pirated content appears online, content owners can initiate forensic analysis. Using specialized detection software, investigators extract the embedded watermark from the pirated copy. The system then matches this watermark to its database of unique identifiers, revealing the original account, session, or device responsible for the leak.
This information provides concrete evidence for legal action. The extracted watermark serves as legally admissible proof, clearly identifying the source and establishing the chain of custody from authorized viewing to unauthorized distribution.
Types of Forensic Watermarking Technologies
Modern content protection employs several forensic watermarking approaches, each with distinct advantages for different use cases.
Server-Side Watermarking
Server-side watermarking represents the most secure approach available today. The system embeds unique identifiers into video content before it reaches the end user, typically during the encoding stage. Each viewer receives a subtly different version of the content, with variations imperceptible to human eyes but detectable by forensic software.
This method excels in security because the watermarking logic never leaves the content provider’s controlled environment. Pirates cannot access or reverse-engineer the embedding process. However, server-side watermarking comes with trade-offs. It requires significant processing power to create unique versions for each user, demands more storage to maintain multiple variants, and can introduce playback delays as the system generates customized streams.
Client-Side Watermarking
Client-side watermarking takes a different approach by applying watermarks on the viewer’s device during playback. The video player or application embeds the unique identifier in real-time as the user watches.
This method offers several advantages. It processes faster since the server sends a single version to all users, scales more efficiently for large audiences, and works particularly well for live content where real-time watermarking is essential. Sports broadcasters and live event streamers frequently choose this approach because extracting watermarks from unauthorized streams happens quickly, allowing for rapid takedown actions.
The security trade-off is notable—client-side logic can potentially be exposed, reverse-engineered, or bypassed by sophisticated attackers. Still, for many applications, the speed and scalability benefits outweigh these concerns.
A/B Watermarking (Session-Based)
A/B watermarking represents one of the most sophisticated approaches to forensic protection. This method divides video content into short segments (typically 2-4 seconds each), with each segment existing in two slightly different versions: Version A and Version B.
The system generates a cryptographically unique sequence for each viewing session. One user might receive segments in the pattern AABABBAB, while another gets BBABAABB. This sequence acts as a binary fingerprint unique to that specific session.
The brilliance of A/B watermarking lies in its balance of security and efficiency. The system only needs to store two versions of each segment, regardless of how many users access the content. When pirated content appears, forensic tools analyze the segment sequence and match it to the original user. This approach provides high security while requiring minimal storage overhead compared to creating unique videos for each viewer.
Blockchain-Enhanced Watermarking
Emerging research has begun integrating blockchain technology with forensic watermarking to create an immutable record of content ownership and distribution. When content is uploaded, its unique watermark and owner information are registered on a blockchain. Smart contracts can then track every access and distribution event, creating a transparent, tamper-proof history of the content’s journey.
This approach enhances copyright protection by providing irrefutable proof of ownership and establishing a clear timeline of authorized distribution. If piracy occurs, the blockchain record can definitively show when and how content was properly distributed, strengthening legal cases against infringers.
Dynamic Watermarks vs. Static Watermarks
Understanding the fundamental differences between dynamic and static watermarks clarifies why modern content protection increasingly favors the dynamic approach.
Static Watermarks: The Traditional Approach
Static watermarks remain constant across all copies of content. Every viewer sees or receives the same mark—perhaps a company logo in the corner, a semi-transparent overlay with the platform name, or an invisible mark embedded once during production.
Static watermarks offer simplicity. They’re easy to implement, require minimal processing power, and don’t demand complex infrastructure. For basic brand protection, where the goal is simply identifying the content owner, static marks serve adequately.
However, static watermarks have critical limitations for anti-piracy efforts. They cannot identify which specific user leaked content—only that it came from your platform generally. Pirates can more easily remove or obscure static marks since they always appear in the same location or pattern. As evidence in legal proceedings, static watermarks provide limited value for tracking individual cases of piracy.
Dynamic Watermarks: The Modern Solution
Dynamic watermarks transform content protection by creating unique identifiers for each viewing session or user. The watermark changes based on who’s watching, when they’re watching, and how they’re accessing the content.
This approach provides unprecedented traceability. When leaked content surfaces, forensic analysis can identify not just that piracy occurred, but pinpoint the exact account, device, and viewing session responsible. This accountability creates a powerful deterrent effect—authorized users think twice before recording or sharing content when they know it can be traced directly back to them.
Dynamic watermarks also resist removal more effectively. Pirates attempting to strip a static watermark from a single location face a straightforward task. But dynamic watermarks that change position every few seconds across thousands of frames require identifying and removing marks from countless locations. The effort often damages the video quality so severely that the pirated copy becomes unwatchable.
The Performance Question
Critics sometimes raise concerns about dynamic watermarking’s computational requirements. Creating unique watermarks for millions of users does demand more processing power and storage than static approaches. However, advances in cloud computing and CDN technology have made this increasingly manageable.
Modern systems using A/B switching can serve millions of users while storing only two versions of each video segment. Session-based watermarking creates unique patterns without requiring unique video files for each user. These efficiencies have made dynamic watermarking practical even for platforms with massive user bases.
Real-World Applications and Success Stories
Forensic video analysis with dynamic watermarking has proven its value across multiple industries, from major entertainment studios to individual course creators.
Hollywood and Entertainment
Major streaming platforms, including Netflix, Disney+, and Amazon Prime Video, deploy forensic watermarking extensively. These services face unique challenges with pre-release content. Screeners sent to critics, award voters, and marketing partners represent high-value targets for pirates who want to release movies before their official premiere.
In one notable case, forensic watermarking prevented what could have been a devastating pre-release leak. When an early copy of a major blockbuster began circulating online weeks before its theatrical debut, forensic analysis extracted the embedded watermark and traced it to a specific reviewer’s account. The investigation revealed that the reviewer’s credentials had been compromised through a phishing attack. The content was quickly taken down, and security protocols were enhanced.
The technology has also transformed how studios handle digital cinema distribution. Each theater projector embeds unique watermarks during playback, combining the projector ID with a timestamp. If someone records the movie with a camcorder, forensic analysis can identify not just which theater but the specific showing where the recording occurred. This capability has significantly reduced camcording piracy.
Online Education and E-Learning
The online education sector has emerged as one of forensic watermarking’s most important beneficiaries. Course creators invest months developing premium content, only to see it leaked on file-sharing sites or sold by content pirates on unauthorized platforms.
A well-known business coach created an exclusive $2,000 course on digital marketing. Within days of launch, the entire course appeared on a piracy forum. Using forensic watermarking, the creator identified that the leak came from a purchaser who had bought access using stolen credit card information. The investigation led to a takedown of the pirated content and provided evidence for law enforcement action.
For educational platforms, the numbers are compelling. Platforms that implemented forensic watermarking reported up to 67% reduction in content piracy within the first year. The technology’s deterrent effect proved as valuable as its detection capabilities—simply informing students that content includes forensic watermarks significantly reduced unauthorized sharing.
Enterprise and Corporate Training
Corporations face unique content security challenges. They develop proprietary training materials, product demonstrations, and internal communications that could damage their competitive position if leaked. A leaked product demo showing unreleased features could alert competitors to strategic plans. Internal corporate communications might contain market-moving information.
A major technology company implemented forensic watermarking across all its internal training and communication videos. When confidential product roadmap information appeared on a tech news site, forensic analysis traced the leak to a specific employee’s viewing session. The investigation revealed the employee had been approached by a competitor seeking insider information. The forensic watermark provided the concrete evidence needed for legal action.
Sports Broadcasting and Live Events
Live sports present particular challenges for content protection. Pirates often restream games in real-time, and the value of sports content degrades rapidly after an event concludes. Traditional watermarking approaches were too slow for live scenarios.
Client-side dynamic watermarking solved this problem. As viewers watch live streams, unique watermarks are embedded in real-time. When illegal restreams are detected, forensic tools can quickly identify the source account. Some platforms can now identify and shut down pirate streams within minutes of detection, significantly reducing the financial impact of live content theft.
A major sports league reported that implementing real-time forensic watermarking with rapid detection protocols reduced illegal streaming by 73% during its championship season. The technology’s speed proved crucial—identifying and shutting down streams within 3-5 minutes made piracy operations unprofitable for many would-be pirates.
Government and Classified Content
Government agencies and defense contractors handle extremely sensitive video content requiring the highest levels of security and accountability. Forensic watermarking provides audit trails showing exactly who accessed classified materials and when.
In one security breach investigation, forensic analysis of leaked government training videos identified the source within hours. The embedded watermarks revealed not just the individual account but the specific date, time, and device used to access the material. This rapid identification allowed security teams to contain the breach and prevent further unauthorized access.
The Technical Process: From Embedding to Detection
Understanding the technical details of forensic watermarking illuminates both its power and its limitations.
Watermark Embedding Techniques
The embedding process uses sophisticated signal processing to hide information within video frames. Several approaches have proven effective.
Frequency Domain Embedding modifies video content in the frequency domain rather than working directly with pixels. The system applies transformations like Discrete Cosine Transform (DCT) or Discrete Wavelet Transform (DWT) to convert video frames into frequency components. Watermark data is then embedded into specific frequency bands that are imperceptible to human vision but resistant to compression and manipulation.
This technique excels at surviving compression because video codecs like H.264 and H.265 work in similar frequency domains. The watermark occupies frequency space that compression algorithms tend to preserve.
Spatial Domain Embedding takes a more direct approach, modifying pixel values to encode watermark information. The system identifies regions in each frame where subtle changes won’t be noticeable—often areas with high texture or rapid motion where human visual perception is less sensitive.
Advanced algorithms use psychovisual modeling to determine the maximum change each pixel can tolerate without creating visible artifacts. The watermark is then distributed across thousands of pixels, with each carrying a tiny fraction of the total information.
Hybrid Approaches combine multiple embedding techniques for maximum robustness. A watermark might be embedded in both frequency and spatial domains, with the spatial watermark providing quick detection and the frequency watermark surviving aggressive attacks.
The Mathematics of Uniqueness
Creating truly unique watermarks for millions of users requires careful cryptographic design. Systems typically use a master secret key combined with session-specific information (user ID, timestamp, device ID) to generate unique watermark patterns.
For A/B watermarking, the system creates a cryptographic hash of the user’s session information, then uses this hash to generate a binary sequence determining which version of each segment to serve. The sequence must be long enough to uniquely identify users—a video with 1,000 segments creates 2^1000 possible combinations, far more than needed even for billions of users.
Detection and Extraction
When pirated content is discovered, the detection process reverses the embedding operation. Detection systems must solve several challenges.
Correlation Analysis compares the suspected pirated video against known watermark patterns. The system extracts features from the video and correlates them against the database of embedded watermarks. When correlation exceeds a statistical threshold, the system identifies the specific watermark present.
Handling Degradation becomes crucial since pirates often compress or manipulate videos. Advanced detection algorithms account for common attacks. They test multiple compression levels, check various aspect ratios and resolutions, analyze cropped regions, and examine temporally resampled versions (frame rate changes).
Synchronization presents another challenge. If pirates re-edit the video, cutting or rearranging scenes, the detector must first synchronize with the original content before extracting watermarks. Systems use content fingerprinting to identify corresponding frames between the pirated copy and the original, even if scenes have been reordered.
Real-Time Detection for Live Content
Live streaming requires specialized detection approaches since the content is both being watermarked and potentially pirated simultaneously. Systems continuously scan known piracy platforms for unauthorized streams. When a suspicious stream is detected, real-time forensic analysis extracts the watermark while the stream is still active.
This rapid detection enables immediate countermeasures. The system can automatically shut down the source user’s account, block their IP address, or issue takedown notices to the piracy platform—often within minutes of detecting the illegal stream.
Limitations and Challenges
Despite its effectiveness, forensic watermarking faces several limitations that content creators should understand.
The Collusion Attack
One of the most serious vulnerabilities is the collusion attack, where multiple pirates compare their copies of the same content to identify and remove watermarks. If pirate A has pattern AABABB and pirate B has pattern BBAABB, they can identify that the third segment differs between their copies. By comparing enough versions, attackers can map all the variation points and create a “clean” copy without any watermarks.
Defense against collusion requires more sophisticated watermarking schemes. Some systems embed watermarks that remain detectable even after averaging multiple copies. Others use anti-collusion codes that can identify participants in collusion attacks. However, these defenses increase computational complexity and aren’t foolproof.
AI and Machine Learning Threats
The rise of artificial intelligence presents new challenges for watermarking. AI models trained on watermark detection might learn to identify and remove forensic marks more effectively than traditional image processing techniques. Generative AI could potentially reconstruct video content, removing watermarks in the process.
Research into adversarial watermarking attempts to address this. These systems design watermarks specifically to resist AI-based removal, often by making the watermark’s removal indistinguishable from content degradation. If removing the watermark also removes essential video information, the pirated copy becomes unwatchable.
Performance and Scalability
Creating unique watermarked versions for millions of simultaneous users demands significant infrastructure. A major streaming service with 100 million subscribers might need to serve billions of unique video segments during peak viewing times.
Cloud computing and CDN integration have made this more manageable, but costs remain substantial. A/B switching reduces storage requirements dramatically compared to creating fully unique versions for each user, but it still demands more resources than serving a single video file to everyone.
The Detection Time Gap
Forensic watermarking is reactive rather than proactive—it identifies piracy after it happens. In the time between a leak occurring and its detection, pirated content may spread widely. For time-sensitive content like sports events or breaking news, even a short delay can result in significant revenue loss.
Some systems have reduced this gap to minutes for live content through automated monitoring and real-time analysis. However, for non-live content, detection often depends on manual discovery of pirated copies, which can take days or weeks.
Legal and Jurisdictional Challenges
Even when forensic watermarking successfully identifies a pirate, taking legal action may prove difficult. If the pirate operates in a jurisdiction with weak intellectual property enforcement or uses anonymization services to hide their identity, the technical success of watermark extraction may not translate to legal consequences.
International cooperation in anti-piracy efforts remains inconsistent. Content owners may identify leakers in countries where pursuing legal action is impractical or impossible, limiting the technology’s real-world deterrent effect.
False Positives and Evidence Standards
Legal proceedings require watermark evidence to meet strict admissibility standards. Defense attorneys may challenge watermark evidence, arguing that extraction methods could produce false positives or that the watermark could have been planted in pirated content to frame an innocent party.
Watermarking systems must demonstrate extremely low false positive rates—ideally zero—to serve as reliable legal evidence. This requires extensive testing and validation, along with transparent documentation of detection methodologies that can withstand legal scrutiny.
The Future of Forensic Video Analysis
The field of forensic video analysis continues to evolve rapidly, with several emerging trends shaping its future direction.
AI-Enhanced Detection
Machine learning is transforming watermark detection, enabling systems to identify marks even after aggressive manipulation. Neural networks can learn the characteristics of watermarked content and detect anomalies that might indicate watermark removal attempts.
Deep learning models are also improving content fingerprinting, allowing systems to match pirated copies to original content even after substantial editing or manipulation. These AI systems can recognize content based on its inherent characteristics rather than relying solely on embedded watermarks, providing redundant protection layers.
Blockchain Integration
The integration of blockchain technology with forensic watermarking creates immutable records of content ownership and distribution. Smart contracts can automatically track content usage, enforce licensing terms, and provide transparent audit trails.
This combination addresses one of watermarking’s key limitations—establishing a chain of custody. When a watermark traces content to a specific user, blockchain records can prove that the user was legitimately provided access, strengthening legal cases by eliminating uncertainty about authorization.
Quantum-Resistant Watermarking
As quantum computing advances, current cryptographic systems face potential vulnerabilities. Researchers are developing quantum-resistant watermarking schemes that will remain secure even against attacks using quantum computers.
These next-generation systems use mathematical approaches that quantum algorithms cannot efficiently break, ensuring watermarking technology remains effective for decades to come.
Perceptual Hashing and Content Authentication
Beyond identifying pirates, forensic video analysis is expanding to combat deepfakes and manipulated content. Perceptual hashing creates unique fingerprints for authentic content, allowing detection systems to identify altered or synthetic videos.
Combining forensic watermarking with deepfake detection creates comprehensive content authentication systems. These systems can verify both that content is genuine (not manipulated) and that it’s authorized (not pirated), addressing multiple threats simultaneously.
Edge Computing and 5G
The rollout of 5G networks and edge computing infrastructure enables more sophisticated real-time watermarking for live and interactive content. Processing can happen closer to users, reducing latency while maintaining security.
This development particularly benefits live streaming and cloud gaming, where traditional server-side watermarking might introduce unacceptable delays. Edge computing allows dynamic watermarking without compromising user experience.
Standardization and Interoperability
Industry efforts toward watermarking standards aim to improve interoperability between different platforms and technologies. Organizations like MovieLabs have published specifications for enhanced content protection, providing frameworks that various implementations can follow.
Standardization benefits the entire ecosystem. Content creators can use watermarking across multiple distribution platforms without implementing completely different systems for each. Detection tools can work with watermarks from various providers, improving the efficiency of anti-piracy operations.
Privacy and Ethical Considerations
As watermarking becomes more sophisticated, privacy concerns grow. Watermarks that track viewing behavior in extreme detail might conflict with privacy regulations like GDPR or CCPA. Future development must balance security needs with user privacy rights.
Some research explores privacy-preserving watermarking that can identify piracy without collecting unnecessary personal information. These systems embed minimal identifying information and use techniques like differential privacy to protect legitimate users while still catching pirates.
Conclusion
Forensic video analysis powered by dynamic watermarks has become an indispensable tool in the fight against digital piracy. In an era where content can be copied and distributed globally within minutes, these invisible guardians provide accountability and traceability that traditional security measures cannot match.
The technology works by embedding unique, imperceptible identifiers into video content—identifiers that survive compression, re-encoding, screen recording, and most pirate manipulation attempts. When leaked content surfaces, forensic analysis can extract these watermarks and trace the leak back to its exact source, providing concrete evidence for legal action.
Real-world applications span the entire digital content ecosystem. Hollywood studios protect pre-release screeners. Online course creators safeguard premium educational content. Corporations secure proprietary training materials. Sports broadcasters combat illegal live streams. Each use case demonstrates the technology’s versatility and effectiveness.
Yet forensic watermarking isn’t perfect. It faces challenges from collusion attacks, AI-powered removal attempts, and the reactive nature of detection. Legal and jurisdictional issues can prevent action even when pirates are successfully identified. These limitations mean watermarking works best as part of a comprehensive security strategy that includes DRM encryption, access controls, monitoring systems, and legal deterrents.
Looking forward, the technology continues to evolve. AI-enhanced detection, blockchain integration, quantum-resistant algorithms, and edge computing promise to make forensic watermarking even more powerful. As pirates develop new techniques, the arms race between content protection and content theft will intensify.
For content creators, the message is clear: protecting digital assets requires multiple layers of defense. Dynamic watermarking won’t prevent every piracy attempt, but it adds crucial accountability that significantly deters unauthorized sharing. When authorized users know their access can be traced definitively, they think twice before recording or distributing content illegally.
The investment in forensic video analysis pays dividends through reduced piracy, recovered revenue, and stronger legal positions when pursuing infringers. In a digital world where content represents substantial business value, these protections aren’t optional—they’re essential for sustainable content businesses.
As we move deeper into 2025 and beyond, forensic video analysis with dynamic watermarking will only grow more sophisticated and necessary. Content creators who implement these technologies now position themselves ahead of threats, protecting their creative investments and revenue streams in an increasingly challenging landscape.
FAQs
Forensic video watermarking embeds invisible, unique markers into videos, allowing content owners to track who leaked content if piracy occurs.
Dynamic watermarks assign session- or viewer-specific data (like user ID or IP) to each stream, enabling identification if a leak is discovered.
Studios, streaming platforms, e-learning providers, and broadcasters use forensic watermarking to deter leaks and trace unauthorized distribution.
Forensic watermarking is invisible and resistant to removal or tampering, unlike visible watermarks, which can be cropped out or blurred.
No, forensic watermarking is embedded at the data level and is imperceptible to viewers, maintaining video quality.
If a pirated copy surfaces, forensic tools can extract the watermark and identify the source within hours.
Dynamic watermarks deter and trace leaks, but no solution can stop all piracy; they strengthen accountability and legal response.
Dynamic watermarks change for each viewer or session, while static watermarks are always the same.
It can include details like user ID, session time, device info, or IP address, all invisible to viewers.
Dynamic forensic watermarks are designed to resist common manipulation, such as cropping or color changes, making removal difficult.
If a leak occurs, the unique watermark is extracted from the pirated video to trace the original viewer or account responsible.