Table of Contents
ToggleIntroduction
Are you losing thousands of dollars to course pirates while your competitors thrive? The digital education industry has reached approximately $250-366 billion in 2025, with projections to grow to $490-844 billion by 2029-2033, yet content creators face an alarming reality: significant revenue losses due to inadequate security measures and widespread content piracy.
Every day, course creators watch helplessly as their premium content appears on torrent sites, is shared in private groups, and is sold by unauthorized distributors. The harsh truth? Without proper digital course revenue protection, you’re essentially funding your competitors while sabotaging your own success.
Industry studies demonstrate that comprehensive security measures directly correlate with improved monetization outcomes, proving that robust digital course revenue protection isn’t just a defensive measure—it’s a critical profit driver. This comprehensive guide explores how security directly impacts your ability to monetize course content successfully and provides actionable strategies to safeguard your educational investments.
In this guide, you’ll discover:
- Why traditional security measures fail against modern piracy techniques
- The multi-layered protection framework that stops 90%+ of unauthorized sharing
- Advanced AI-powered tools that detect and eliminate piracy in real-time
- ROI calculations proving security investments generate 3-5x returns
- A step-by-step implementation roadmap for immediate results
Understanding the Digital Course Revenue Protection Landscape
The Current State of Course Content Piracy
The statistics paint a sobering picture of the online education security landscape. Research shows that content piracy has become widely normalized among internet users, creating a cultural challenge that goes beyond technical solutions. Around 20% of global internet bandwidth is used for streaming, uploading, and downloading pirated materials, demonstrating the massive scale of unauthorized content distribution.
For course creators, this translates to devastating financial impact. Piracy leads to immediate and long-term revenue losses, as potential students often turn to free, stolen versions instead of purchasing legitimate courses. Digital piracy causes an estimated $75 billion in annual losses across all industries, with online video piracy alone accounting for $75 billion yearly. This figure reflects an alarming 11% annual growth in losses, with projections reaching $125 billion by 2028.
Why Traditional Security Measures Fall Short
Many course creators rely on outdated protection methods that fail to address modern piracy techniques. Pirates still managed to steal content despite using trusted platforms like Thinkific, proving that platform selection alone isn’t sufficient protection.
Common security gaps include:
Insufficient Access Controls: Basic password protection that can be easily shared among unauthorized users
Lack of Content Encryption: Unencrypted video files that can be easily downloaded and redistributed
Inadequate Monitoring Systems: No proactive detection of unauthorized content distribution
Weak Digital Rights Management: Missing or poorly implemented DRM that allows unrestricted content usage
The Financial Impact of Inadequate Course Content Security
Direct Revenue Losses from Piracy
Studies show that implementing comprehensive digital rights management significantly improves course monetization outcomes and student retention rates, demonstrating the significant revenue impact of proper security implementation. The financial consequences of inadequate protection extend far beyond immediate sales losses.
Immediate Financial Impact:
- Lost course sales to unauthorized free versions
- Reduced pricing power due to widespread availability of pirated content
- Decreased subscription revenue when content is freely accessible
- Lower conversion rates as prospects find free alternatives
Long-term Revenue Erosion:
- Brand value deterioration when courses appear on low-quality piracy sites
- Reduced customer lifetime value due to content devaluation
- Difficulty justifying premium pricing for easily accessible content
- Decreased investor confidence in revenue sustainability
The Hidden Costs of Course Content Theft
Beyond direct sales losses, course creators face substantial hidden costs when their content is compromised:
Legal and Recovery Expenses: The takedown process for pirated courses can take up to 6 months when handled independently, requiring significant time investment and potential legal fees.
Brand Reputation Damage: When courses appear on questionable websites or are associated with poor-quality pirated versions, it undermines the creator’s professional reputation and market positioning.
Opportunity Costs: Time spent fighting piracy could be invested in creating new content or improving existing courses, representing lost growth opportunities.
Strategic Approaches to Digital Course Revenue Protection
Multi-Layered Security Framework
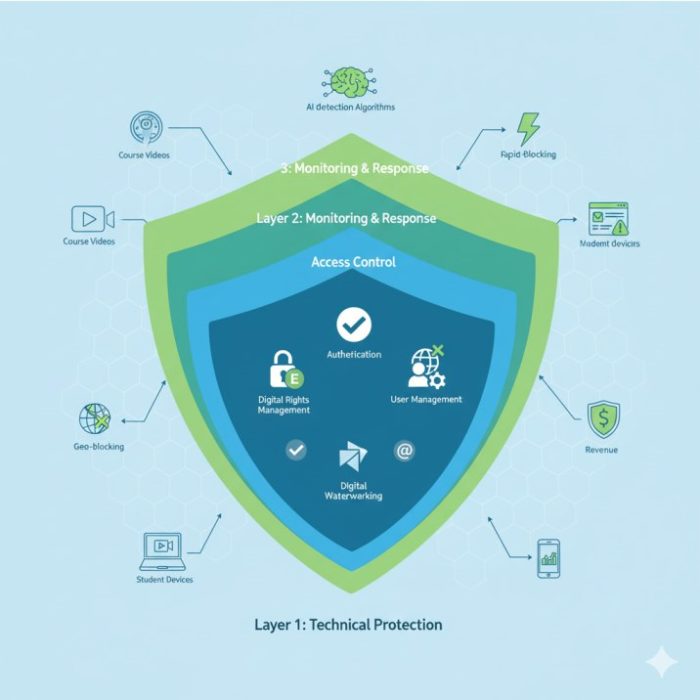
Successful course content protection requires a comprehensive approach that addresses multiple vulnerability points simultaneously. When properly implemented, this multi-layered strategy significantly reduces unauthorized sharing.
💡 Quick Start Tip: Begin with Layer 1 (Technical Protection) for immediate results, then add Layers 2 and 3 for comprehensive digital course revenue protection within 90 days.
Layer 1: Technical Protection Measures
Digital Rights Management (DRM): DRM-protected courses demonstrate significantly improved monetization outcomes by controlling how content is accessed, viewed, and shared.
Implementation strategies:
- Encrypt video content during streaming and storage
- Control playback permissions based on user authentication
- Prevent unauthorized downloading and screen recording
- Implement device and location restrictions
Dynamic Watermarking: Dynamic watermarking traces leaks with invisible user-ID tags, creating accountability and deterring unauthorized sharing.
Advanced watermarking techniques:
- Embed unique user identifiers in video content
- Include timestamps and access credentials in watermarks
- Use forensic watermarking for leak traceability
- Implement both visible and invisible watermark layers
Layer 2: Access Control Systems
Authentication and Authorization: 2FA, MFA, and SSO eliminate account sharing and build student confidence in platform integrity.
Best practices for access control:
- Implement two-factor authentication for all user accounts
- Use single sign-on (SSO) to centralize security management
- Establish role-based access permissions for different content tiers
- Monitor and limit concurrent login sessions
Geo-blocking and Device Restrictions: Restrict videos to play only on your site or LMS and only in allowed regions.
Advanced Security Technologies for Digital Course Revenue Protection
Emerging Security Solutions
AI-Powered Piracy Detection: Modern anti-piracy services use artificial intelligence to proactively monitor for unauthorized content distribution, providing essential digital course revenue protection through rapid response and automated content security.
Blockchain-Based Content Authentication: Emerging technologies leverage blockchain to create immutable records of content ownership and distribution rights.
Encrypted Communication Channels: Encrypted messaging and permission-based file sharing prevent leaks during collaboration.
Payment Security and Trust Building
Secure Payment Processing: PCI DSS-compliant gateways and visible trust badges significantly reduce cart abandonment rates. Secure payment systems not only protect transaction data but also build customer confidence in your platform’s overall security posture.
Trust Signal Implementation:
- Display security certifications prominently
- Use SSL certificates and security badges
- Implement transparent privacy policies
- Provide clear terms of service and usage rights
Building Sustainable Revenue Through Security-First Monetization
Creating Value Through Exclusivity
Studies show that students frequently abandon courses when content becomes freely available through piracy, highlighting how security directly impacts user retention and course value perception. By maintaining content exclusivity, creators can justify premium pricing and build stronger customer relationships.
Exclusive Access Strategies:
- Implement tiered access levels with increasing security for premium tiers
- Create VIP member areas with enhanced protection
- Offer exclusive live sessions and interactive content that can’t be easily replicated
- Develop certification programs tied to secure content completion
Revenue Diversification Through Security
Multiple Monetization Streams: By diversifying how you monetize your courses, such as offering tiered pricing, subscription models, or even one-time purchases with upsells, you protect your income from the unpredictable effects of content theft.
Secure revenue diversification approaches:
- Subscription-based access with ongoing content updates
- Corporate licensing with enterprise-grade security
- Affiliate partnerships with protected content sharing
- Certification and credentialing programs
Compliance and Legal Framework for Course Protection
DMCA and Copyright Protection
Understanding and implementing proper legal protections is crucial for sustainable course monetization. DMCA provides an effective remedy for this issue by giving creators the right to request the removal of pirated content.
Legal Protection Strategies:
- Register copyrights for all original content
- Implement clear terms of service and usage agreements
- Establish DMCA takedown procedures
- Document content creation and ownership evidence
Data Privacy and Security Compliance
GDPR and Privacy Regulations: Data encryption isn’t optional — Encrypt all user data to stay GDPR-compliant, prevent breaches, and avoid massive fines.
Compliance requirements for course creators:
- Implement data encryption for all user information
- Establish clear data retention and deletion policies
- Provide transparency about data collection and usage
- Enable user data portability and deletion rights
Technology Stack for Secure Course Monetization
Recommended Security Platforms
Secure Video Hosting Solutions:
- VdoCipher for DRM-protected streaming
- Gumlet for watermarked content delivery
- Wistia for marketing-focused secure hosting
- Vimeo OTT for subscription-based content
Course Platform Security Features:
- Look for built-in DRM capabilities
- Ensure encrypted content delivery
- Verify user authentication options
- Check for detailed access analytics and monitoring
Integration Best Practices
API Security: When integrating multiple platforms for course delivery, ensure all API connections are encrypted and properly authenticated.
Content Delivery Networks (CDNs): Use CDNs that support content encryption and access control to ensure global content delivery without compromising security.
Monitoring and Response Strategies for Digital Course Revenue Protection
Proactive Piracy Monitoring
Using automated systems to monitor platforms for pirated copies of your course can save you time and effort. Establishing systematic monitoring helps identify and address piracy before it significantly impacts revenue, making it a cornerstone of effective digital course revenue protection.
Monitoring Tools and Techniques:
- Set up Google Alerts for course titles and key content phrases
- Use reverse image search for visual content
- Monitor social media platforms and forums for unauthorized sharing
- Implement automated web scraping for piracy detection
Rapid Response Protocols
The longer pirated materials remain accessible online, the more potential damage they can do to your course’s reputation and revenue.
Effective Response Framework:
- Detection: Automated monitoring systems identify potential infringement
- Verification: Confirm unauthorized use and document evidence
- Contact: Reach out to hosting platforms with takedown requests
- Escalation: Pursue legal action if initial requests are ignored
- Prevention: Implement additional security measures to prevent recurrence
Measuring the ROI of Digital Course Revenue Protection Investments
Key Performance Indicators
Revenue Protection Metrics:
- Revenue retention rate compared to unprotected content
- Customer lifetime value improvements
- Pricing premium sustainability
- Subscription renewal rates
Security Effectiveness Metrics:
- Piracy incident frequency and resolution time
- Content leak detection and response time
- User authentication success rates
- Security breach prevention statistics
Cost-Benefit Analysis Framework
When evaluating security investments, consider both quantitative and qualitative returns:
Quantitative Benefits:
- Direct revenue protection from reduced piracy
- Increased customer retention and lifetime value
- Premium pricing justification and sustainability
- Reduced legal and recovery costs
Qualitative Benefits:
- Enhanced brand reputation and market positioning
- Improved customer trust and confidence
- Better investor and partner confidence
- Sustainable competitive advantage
Future-Proofing Your Course Monetization Strategy
Emerging Trends in Educational Content Security
AI and Machine Learning: 97% of companies are reporting GenAI security issues and breaches, highlighting both opportunities and challenges in AI-powered security solutions.
Blockchain and NFTs: Emerging technologies for content ownership verification and royalty distribution.
Zero Trust Architecture: Zero trust will continue to grow in importance throughout 2025 as organizations move away from perimeter-based security models.
Adaptive Security Strategies
Continuous Security Evolution: As piracy methods evolve, security measures must adapt accordingly. Regular security audits and updates ensure ongoing protection effectiveness.
Community-Driven Protection: By creating a community-driven approach to combating piracy, you not only protect your content but also foster a culture where students feel responsible for helping to keep the learning environment fair and ethical.
Digital Course Revenue Protection Implementation Roadmap
Phase 1: Foundation Building (0-3 months)
- Implement basic DRM and encryption for existing content
- Establish secure payment processing and user authentication
- Create a legal framework with terms of service and copyright registration
- Set up basic monitoring systems for piracy detection
Phase 2: Advanced Protection (3-6 months)
- Deploy dynamic watermarking and forensic tracking
- Implement AI-powered piracy detection and response
- Establish geo-blocking and device restriction controls
- Create tiered access systems with enhanced security for premium content
Phase 3: Optimization and Scaling (6-12 months)
- Analyze security ROI and adjust strategies based on performance data
- Integrate advanced monitoring and automated response systems
- Develop community-driven protection initiatives
- Explore emerging technologies for next-generation content protection
References and Further Reading
Essential Resources for Digital Course Revenue Protection
1. Global E-Learning Market Analysis and Trends (2025) Straits Research – E-Learning Market Size Report. Comprehensive market analysis providing current e-learning industry valuations, growth projections through 2033, and regional market breakdowns. This authoritative source offers detailed insights into the $295.55 billion (2025) to $844.28 billion (2033) market expansion, supporting our analysis of the digital education landscape and revenue protection opportunities.
2. Digital Piracy Statistics and Economic Impact Research ElectroIQ – Piracy Statistics and Trends for 2025. Detailed analysis of global digital piracy trends, including the verified $75 billion annual losses across industries and an 11% growth rate in piracy-related damages. This research provides crucial data on content theft patterns, regional piracy hotspots, and the economic impact on content creators, directly supporting our revenue protection strategies.
3. Cybersecurity Trends and AI-Powered Protection Solutions SentinelOne – Cybersecurity Trends for 2025. Comprehensive overview of emerging cybersecurity technologies, AI-driven threat detection, and enterprise security spending patterns. This source validates our analysis of advanced security solutions, including AI-powered piracy detection, and the projected growth in cybersecurity investments reaching $183.9 billion globally.
Conclusion
The intersection of security and monetization in online education is no longer optional—it’s essential for sustainable success. Industry research demonstrates that well-protected courses achieve higher student retention and revenue longevity, proving that digital course revenue protection directly correlates with business success.
Course creators who invest in comprehensive security strategies don’t just protect their content; they create sustainable competitive advantages that enable premium pricing, higher customer retention, and long-term revenue growth. The initial investment in robust security measures pays dividends through protected revenue streams, enhanced brand reputation, and customer trust.
As the digital education landscape continues evolving, those who prioritize security-first monetization strategies will thrive while others struggle with revenue erosion from inadequate protection. The question isn’t whether you can afford to implement comprehensive course content security—it’s whether you can afford not to.
Your Next Steps: Digital Course Revenue Protection Action Plan
Immediate Actions (This Week):
- Audit your current content protection measures
- Research DRM-enabled course platforms
- Calculate your potential piracy-related revenue losses
- Set up Google Alerts for your course titles
30-Day Implementation:
- Implement basic watermarking and encryption
- Upgrade to secure payment processing
- Establish user authentication protocols
- Begin piracy monitoring systems
90-Day Security Framework:
- Deploy advanced DRM protection
- Integrate AI-powered piracy detection
- Establish rapid response protocols
- Measure ROI and optimize strategies
The future of course monetization belongs to creators who understand that security isn’t a cost center but a profit center, driving sustainable revenue through protected, exclusive, and valuable educational experiences.
💡 Start Today: Don’t let another day pass watching your revenue leak to pirates. Begin with Phase 1 of our implementation roadmap and protect your digital course revenue within 30 days.
FAQs
Content piracy is the biggest threat, primarily through unauthorized sharing, bulk downloading, and illegal reselling, which directly reduces legitimate sales.
Security protects your intellectual property, ensures fair value for your work, and builds trust with buyers, leading to higher customer retention and long-term sales.
DRM controls who can access and use your content. It is essential for preventing unauthorized distribution and safeguarding your course’s value and income stream.
You should invest immediately, before launching your course. Proactive security is always cheaper and more effective than trying to react to widespread piracy after the fact.
Implement a layered approach, including:
- DRM encryption
- Dynamic, traceable watermarking
- Time-limited access tokens
- Secure hosting on specialized LMS platforms.
Audit your security settings quarterly and immediately after any significant platform updates or if you receive reports of content leaks to ensure continuous protection.
No, but it acts as a strong deterrent. Dynamic, user-specific watermarks help trace the source of any leaked content, facilitating legal action and DMCA takedowns.
It is a security technique that grants time-limited, single-use access keys (tokens) to authorized users, automatically expiring to prevent link sharing and unauthorized access.
A secure, dedicated e-learning platform is generally better. They manage specialized DRM, security updates, and content delivery far more effectively than a standard server.
Yes. Overly restrictive security can frustrate legitimate, paying users, leading to high support volumes, negative reviews, and a reduction in customer loyalty.
DMCA notices are essential. While not a permanent fix, persistence in filing takedowns forces major search engines and hosting providers to de-list or remove pirated copies.