Table of Contents
ToggleThe Security-Convenience Balance for Multi-Device Course Access in 2025
Online course creators and educational coaches face a dilemma: they must offer students the convenience of multi-device access—allowing them to watch content on a laptop, tablet, or phone—while simultaneously protecting their intellectual property from theft and piracy. If the security is too restrictive, it frustrates the customer and damages the learning experience. If the access is too easy, your premium content ends up on torrent sites.
The solution lies in adopting real security for real creators, which means moving beyond fragile, false confidence solutions and implementing enterprise-grade security that maintains a seamless user experience. Here is a breakdown of how the right video hosting partner can provide uncompromising security without sacrificing global performance or universal compatibility.
1. Uncompromising Security: Ending Credential Sharing with DRM
One of the greatest threats to recurring revenue for course creators is login credential sharing. A single student account can be shared with dozens of people, essentially stealing your course. To solve this, you need security features that are paranoid about content protection in the best way possible:
Hollywood-Grade DRM Encryption: Digital Rights Management (DRM) is the fundamental layer of unbreakable content protection. Solutions like Google Widevine and Apple FairPlay are embedded into the video stream to ensure the video file cannot be downloaded in a usable form, preventing actual piracy, not just casual downloading.
Concurrent Login Control: To stop shared accounts, the video system must enforce strict device limits. This feature monitors the number of devices (e.g., a laptop, two phones) actively logged into a single user account. If a student tries to log in on a fourth device, the system automatically revokes access from the oldest device, eliminating the viability of sharing credentials for a monthly fee.
Geo-Restriction & IP Fencing: For creators selling in specific markets, the system can restrict course playback to predefined geographies or even specific IP addresses, providing an extra layer of protection for exclusive content.
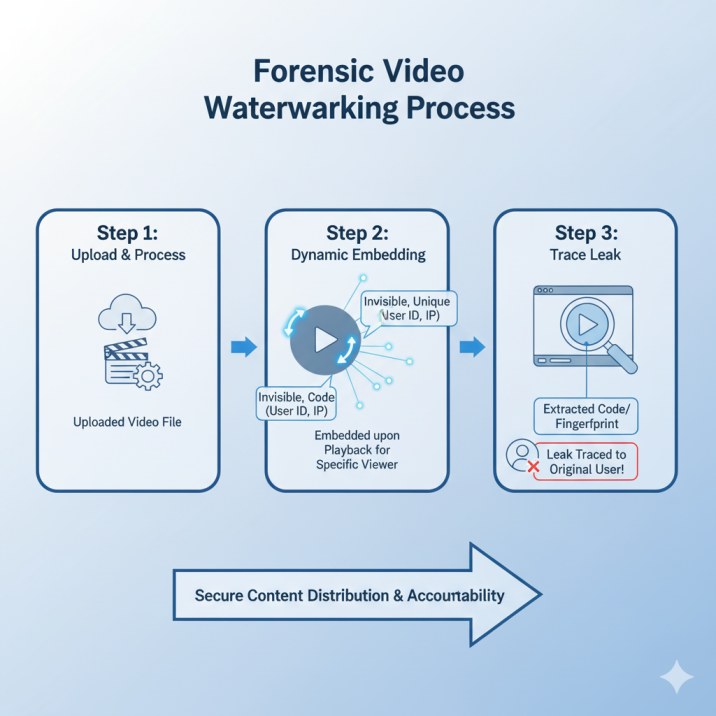
2. Forensic Tracking: Tracing Leaks with Dynamic Watermarking
While DRM prevents most unauthorized downloading, the most aggressive pirates resort to screen recording. This is where a dynamic, forensic-grade tracking system is essential to protect high-value course content.
Forensic Watermarking works by dynamically embedding an invisible, unique fingerprint into the video stream for every single viewer.
How Inkrypt Videos’ Forensic Watermarking Traces Piracy to the Source
Unique Signature Generation: When a user clicks play, the system instantly generates a unique code (their user ID, IP address, and a timestamp) for that specific session.
Invisible Embedding: This unique code is then imperceptibly woven into the video frames. The watermark remains invisible to viewers and does not affect video quality.
Leak Tracing: If a screen-recorded copy of the content is later found online, the publisher can upload the pirated file to a forensic extraction tool. This tool quickly analyzes the video to retrieve the invisible code/fingerprint, instantly identifying the original student/account that leaked the content.
This system acts as a massive deterrent, as potential leakers know that any content theft can be traced directly back to their account, enabling prompt legal action.
3. Universal Compatibility: Making Security Seamless
Security is useless if it creates technical complexity for the creator or playback issues for the student. The solution must be performance-driven and easy to integrate:
Zero-Jargon Integration: Enterprise-level power does not need to mean enterprise-level complexity. Modern solutions offer a 30-minute integration via simple APIs and WordPress plugins, rather than the weeks or months of development required by traditional security providers.
Global, Zero-Buffering Performance: Security measures should never compromise delivery speed. By leveraging global Content Delivery Networks (CDNs) like Amazon CDN, the video content is distributed from the closest server to the student, guaranteeing zero buffering worldwide.
Universal Device Support: Your solution must ensure every student can access the course, regardless of their hardware. This includes providing universal compatibility for older devices often ignored by competitors, ensuring the professional learning experience is maintained for all users.
By adopting a platform that combines multi-DRM encryption, forensic tracking, and global performance with an easy setup, course creators can focus on scaling their business while having peace of mind that their premium content is bulletproof.
Resources and Citations
The security protocols and strategic considerations for balancing content protection with user access were informed by research from the following external industry and technical authorities:
Digital Rights Management (DRM) Explained – Fortinet provides a comprehensive overview of how Digital Rights Management technology works, its purpose in preventing unauthorized distribution and modification of digital content, and its crucial role for content creators and copyright holders.
Video Watermarking – IEEE Xplore: An authoritative technical publication outlining advanced techniques, such as A/B watermarking, used for real-time video stream protection. It validates the goal of forensic watermarking: to trace unauthorized redistribution back to the source user.
Is cybersecurity incompatible with digital convenience? – McKinsey explores the fundamental challenge facing digital content providers: finding the balance between strong security measures and seamless user experience. It discusses tailoring security based on customer preference and risk segmentation.
Conclusion
The age of forcing course creators to choose between a convenient student experience and effective content protection is finally over. By implementing a modern video solution that seamlessly integrates multi-DRM encryption, concurrent login control, and forensic watermarking, you are not just building a simple paywall—you are making a critical investment in the long-term, scalable growth of your coaching business.
Real security for real creators means providing a flawless, universally accessible learning experience while simultaneously future-proofing your revenue against evolving piracy threats and putting an end to credential sharing and illegal downloads.
Ready to Protect Your Premium Content?
Stop losing revenue to shared logins and piracy today. Protect your intellectual property with the same unbreakable, forensic-grade security used by major media companies, made simple for online course creators.
Schedule your free 30-minute integration demo with Inkrypt Videos and start protecting your content immediately.
FAQs
You must use concurrent login control to limit active sessions per account. The system automatically revokes access on the oldest device when a new one logs in.
Implement dynamic forensic watermarking. This embeds a unique, invisible user ID into the video, allowing you to trace the content leak back to the original account.
Standard passwords cannot prevent unauthorized downloads, screen recording, or credential sharing. You need DRM encryption to protect the actual video stream itself.
True security uses Multi-DRM (Widevine/FairPlay) to authenticate the device, not just the user, ensuring fast, seamless playback on all major devices up to a set limit.
The video stream is encrypted and requires a device license key to play. An unauthorized download attempt will result in a corrupted, unusable file.
Content protection should be implemented before launch. Securing your course from day one maximizes revenue from initial sales and establishes your content’s long-term value.
No. Modern DRM utilizes global Content Delivery Networks (CDNs) to distribute the protected video, ensuring fast, zero-buffering performance regardless of the student’s location.
No, forensic watermarking is an imperceptible, unique digital fingerprint embedded within the video stream, invisible to the viewer.
Simple encryption secures storage; Multi-DRM secures playback on specific authorized devices using complex license keys (Widevine, FairPlay).
Yes, you can set granular policies to limit access to a single device type or restrict the total number of unique devices a user can register for access.
No. These platforms do not offer enterprise-grade Multi-DRM or forensic watermarking, leaving your high-value course content vulnerable to easy downloading and piracy.