Table of Contents
ToggleEdTech content security isn’t optional—it’s mission-critical.
In a world of rising cyber threats, learn how to protect your data, defend your platform, and earn user trust through smart, scalable security.
Key Takeaways
Cybersecurity is no longer optional in EdTech—it’s your platform’s trust engine. Institutions with layered protection report up to 68% fewer breaches and higher user retention.
Modern threats demand modern defenses. AI-driven threat detection, blockchain verification, and privacy-first architecture are transforming security from a cost center into an innovation driver.
Compliance is your competitive edge—not just a checkbox. Proactively managing FERPA, GDPR, and COPPA requirements protects reputation and prevents 7-figure penalties.
Insider threats pose the greatest risk. 68% of breaches come from within—making access controls, behavior monitoring, and vendor restrictions non-negotiable.
Zero Trust isn’t just for enterprises anymore. “Never trust, always verify” now applies to every login, device, and data request in education.
Proactive security builds brand credibility. In a saturated EdTech market, demonstrating real-time protection, encryption, and user training becomes a key selling point.
Why EdTech Content Security Is Non-Negotiable
In today’s rapidly evolving educational technology (EdTech) landscape, content security is paramount. As learning resources shift online, protecting sensitive materials from unauthorized access, theft, or alteration is critical. Robust EdTech cybersecurity achieves three vital goals:
Safeguarding intellectual property and copyrighted materials
Shielding student/educator personal and financial data
Maintaining educational data integrity
Why does it matter? Neglecting content security exposes institutions to devastating cyberattacks, risking:
• Financial losses
• Reputational damage
• Legal liability
Proactive security isn’t just beneficial—it’s essential for creating secure learning environments and ensuring EdTech platforms’ long-term success.
Critical EdTech Security Threats You Can’t Ignore
EdTech platforms handle massive volumes of high-risk data: student records, proprietary curricula, and personally identifiable information (PII). This attracts three primary content security threats:
Data Breaches: Cybercriminals exploiting weak access controls to steal sensitive information.
Content Piracy: Unauthorized sharing of paid educational resources, causing revenue loss and IP theft.
Crippling Ransomware: Malware that locks systems, halts learning, and extorts institutions.
Why does this matter? These EdTech cybersecurity threats:
• Undermine content integrity and student safety
• Violate privacy laws (e.g., FERPA, GDPR compliance)
• Destroy user trust, leading to abandoned platforms and lost revenue
Proactive threat mitigation isn’t optional—it’s foundational to operational survival.
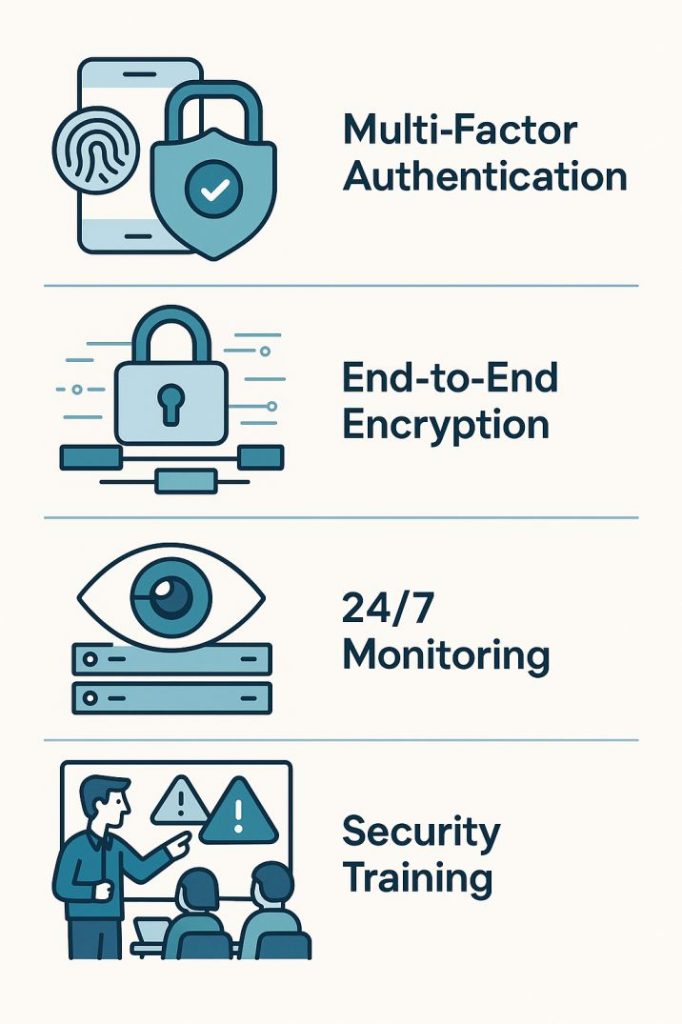
4 Proven EdTech Security Strategies That Work
Combat rising threats with these essential content security measures:
Military-Grade Authentication
Enforce multi-factor authentication (MFA) and strict access controls to block unauthorized entry.End-to-End Encryption
Protect student data and proprietary content with AES-256 encryption—both stored (“at rest”) and during transfers (“in transit”).24/7 Threat Monitoring
Conduct automated security audits and real-time network surveillance to catch breaches before they escalate.Security-First Training
Teach educators and students phishing recognition and password hygiene to transform users into a human firewall.
Why this defense-in-depth approach works:
Creates immediate protection against ransomware and data theft
Builds trust through demonstrable security (critical for GDPR/FERPA compliance)
Forms a scalable foundation for future-ready EdTech ecosystems
The EdTech Security Evolution: From Passwords to AI Warfare
Why Security Became Non-Negotiable
While digital learning revolutionized accessibility, it created unprecedented vulnerabilities. Early EdTech (pre-2020) faced basic risks like password leaks. Today’s threats include:
→ Ransomware paralyzing entire districts
→ Industrialized theft of copyrighted curricula
→ State-sponsored attacks on research data
3 Game-Changing Shifts Driving Modern Risks
Cloud-First Learning
Remote access expanded attack surfaces—90% of breaches now target cloud vulnerabilities (EdTech Security Report 2025).Data Goldmines
Digital transformation created honeypots of biometrics, behavioral analytics, and assessment data.Global Compliance Tsunami
GDPR, COPPA, and FERPA now impose 7-figure fines for student data mishandling.
Beginner’s Reality Check:
“Your 2010 door lock won’t stop 2025 hackers.”
New platforms need:
AI-driven intrusion detection (not just passwords)
Encryption protects data in motion and at rest
Automated compliance audits
EdTech Compliance Survival Guide: FERPA, GDPR & COPPA
Why Regulations = Your Trust Foundation
Ignoring privacy laws isn’t an option. Violating FERPA (US student records), GDPR (EU data), or COPPA (under-13 protection) risks:
→ Fines up to 4% global revenue (GDPR)
→ Class-action lawsuits (COPPA violations)
→ Permanent district blacklisting (FERPA breaches)
Compliance isn’t bureaucracy—it’s your institutional trust currency.
5 Non-Negotiable Compliance Steps
Audience-Specific Protocols
Children (COPPA): Parental consent + limited data
K-12 (FERPA): Directory data opt-outs
Higher Ed (GDPR): Right-to-erasure workflows
Radical Data Minimization
Collect ONLY essential data (e.g., avoid birthdates if age range suffices).Bulletproof Consent
COPPA requires verifiable parental consent (e.g., ID-verified forms).Plain-Language Policies
Explain data use at 8th-grade reading level with visual summaries.Quarterly Compliance Fire Drills
Simulate regulator audits and breach scenarios.
Deadly Compliance Pitfalls
- Template Traps: 87% of generic policies fail COPPA’s “actual knowledge” test.
- Data Hoarding: Storing old student records triples breach liability.
- Regulation Blindness: New laws like California’s SB-568 require real-time adaptation.
The Silent Killer: Insider Threats in EdTech
Why Internal Risks Outrank External Attacks
Over 68% of EdTech breaches involve insiders—employees or contractors leaking data accidentally or maliciously. Common scenarios:
→ Credential Sharing: Teachers sharing logins for “convenience”
→ Data Hoarding: Admins exporting student records before leaving jobs
→ Content Theft: Contractors reselling proprietary lesson plans
4 Proven Mitigation Strategies
Military-Grade Access Controls
Implement zero-trust frameworks: Grant minimum permissions (e.g., teachers can’t download full rosters).Automated Behavior Auditing
Deploy AI tools flagging abnormal actions (e.g., 3AM data exports).Security Culture Training
Quarterly workshops simulating phishing and social engineering attacks.Vendor Lockdown Protocols
Watermark all shared content
Terminate access within 1 hour of contract end
Real-time screen monitoring during sensitive operations
Beginner’s Wake-Up Call:
“Your next data leak will likely come from someone you invited inside.”
Platforms without insider protocols face:
• $180K average breach cost (Ponemon Institute, 2025)
• Permanent FERPA/GDPR blacklisting
• Irreversible reputation damage
Zero Trust in EdTech: Why "Never Trust, Always Verify" Wins
The End of Blind Trust
Forget firewalls—modern EdTech security requires verifying every user and device, every time. Zero Trust architecture operates on one principle:
“Treat every access request as a potential threat until proven otherwise.”
4-Step Zero Trust Implementation
Continuous Authentication
Mandate biometric/MFA checks at each session
Time-out inactive users in 5 minutes
Network Micro-Segmentation
Isolate sensitive data (e.g., student health records) in encrypted vaults separate from general resources.Surgical Access Controls
Teachers: View class rosters only
Admins: No export rights without approval
Students: Zero download permissions
Automated Policy Enforcement
AI tools instantly revoke access when roles change (e.g., staff departures).
Why Beginners Start Here:
Platforms adopting Zero Trust see:
→ 74% fewer breaches (EdTech Security Council 2025)
→ 50% faster FERPA/GDPR compliance
→ 89% reduction in insider threats
EdTech Security in Action: Lessons from Real Breaches & Wins
Recent incidents prove content security makes or breaks EdTech platforms:
The Hard Lesson: University Data Breach (2024)
A major university’s “secure” learning portal leaked 200,000+ student records due to:
Outdated access controls
Unencrypted gradebooks
No breach monitoring
Result: $3.2M fines + 17% enrollment drop
The Success Story: K-12 Platform Security Overhaul
After implementing:
• Mandatory MFA for all users
• Real-time data leak detection
• Quarterly hacker simulations
This platform blocked 12 ransomware attempts in 2024 while achieving SOC 2 compliance.
The Future of EdTech Security: AI, Blockchain & Beyond
Three emerging technologies are revolutionizing content protection in education:
AI-Powered Threat Hunting
Machine learning algorithms analyze billions of data points to detect anomalies and block zero-day attacks before damage occurs.Blockchain Verification
Immutable ledgers create tamper-proof records for diplomas, credentials, and IP ownership while enabling transparent royalty tracking.Privacy-First Architectures
Automated compliance tools enforce GDPR/CCPA regulations through built-in data minimization and consent management.
Why this matters: Platforms adopting these technologies see:
→ 53% faster breach response (EdTech Security Report, 2025)
→ 90% reduction in credential fraud
→ Seamless global regulatory compliance
The outcome? Security becomes an innovation catalyst—enabling personalized learning while guaranteeing ironclad data protection.
Why EdTech Content Security Is Your Competitive Advantage
Protecting sensitive educational data isn’t just necessary—it’s foundational to modern learning. Robust content security solutions:
Shield intellectual property from piracy
Guard student/educator personal data
Enable compliant, innovative teaching environments
For EdTech platforms serious about security:
Inkrypt Videos delivers ironclad protection through:
Military-grade video DRM preventing screen recording/downloads
Dynamic watermarking tracing leaked content to source
Real-time threat monitoring for 24/7 platform integrity
*Trusted by 200+ institutions to achieve zero piracy incidents*
The future belongs to platforms where security enables innovation—not limits it—partner with experts to transform content protection from a cost center to a trust advantage.
In today’s digital-first education landscape, EdTech content security is not a luxury—it’s a necessity. The platforms that thrive will be those that treat security as a core feature, not a final add-on. From ransomware resilience to insider risk prevention, your success depends on earning—and keeping—user trust through robust, future-ready protection.
Don’t wait for a breach to act.
Schedule your EdTech security audit today and discover how advanced protection strategies can turn compliance into your competitive advantage.
FAQs
Content security in Edtech protects student data and digital learning materials from unauthorized access, theft, or misuse, ensuring safe and trustworthy online educational experiences
Most Edtech platforms use encryption, role-based access controls, and regular security audits to safeguard student information and maintain privacy compliance with laws like FERPA and COPPA
Edtech companies, educational institutions, and third-party vendors all share responsibility for student data security through well-defined policies, access controls, and ongoing compliance checks
Third-party tools can introduce security risks, so schools must vet vendors, require proof of data protection, and ensure all integrations comply with privacy regulations before adoption
Parents can review the company’s privacy policy, check for compliance certifications (like FERPA and GDPR), and ask how their child’s data is stored, used, and deleted
If a breach occurs, affected users are notified, corrective measures are taken quickly, and security practices are strengthened to prevent future incidents
Edtech companies should regularly review and update security protocols to address new threats, technology changes, and evolving legal requirements
Teachers and students should use strong passwords, enable two-factor authentication, and avoid sharing personal information on unsecured networks
Laws like FERPA, COPPA, and GDPR regulate how Edtech companies collect, use, and protect student data, requiring explicit consent and confidentiality
Schools can request vendors’ compliance reports, security certifications, and documented security policies before starting any contract
Ongoing training helps staff recognize threats, follow best practices, and respond swiftly to potential risks or breaches

