Table of Contents
ToggleIs your backup strategy ready for 2025’s cyber threats? Discover essential backup solutions and security protocols to protect your data, media, and business from evolving digital disasters.
Key Takeaways: Your 2025 Digital Survival Strategy
Adopt a Hybrid Backup Model (3-2-1 Rule): Combine local, cloud, and air-gapped storage to safeguard data from ransomware, physical damage, and insider threats. Automate backups and test recovery monthly.
Fortify with Immutable & Zero-Trust Backups: Use WORM-compliant cloud storage and enforce MFA to prevent malicious deletion or unauthorized access to critical assets.
Encrypt Everything, Intelligently: Deploy full disk and file-level encryption, and audit tools quarterly. Pre-encrypt files before cloud uploads to ensure end-to-end data security.
Upgrade Password Policies Company-Wide: Require unique, complex passphrases and mandate password manager use to combat the 81% of breaches caused by reused credentials.
Implement Predictive Patching & Smart Updates: Address critical vulnerabilities within 24 hours using AI-powered tools, and test all updates in staging to balance performance and security.
Make Cyber Education Ongoing, Not Optional: Regular phishing simulations, KPI tracking, and VR-based threat exercises foster a resilient, security-conscious workforce.
Leverage Blockchain & WORM for Media Integrity: Use blockchain for timestamped ownership and WORM for ransomware-proof archiving. Ideal for compliance and creative IP protection.
Deploy Full-Stack Zero-Trust Security: Integrate AI monitoring, micro-segmentation, and JIT access to reduce breach risk by over 90%, especially for sensitive media environments.
Backup Solutions: Your 2025 Digital Survival Strategy
Robust data backup isn’t just IT hygiene—it’s business continuity armor. With ransomware attacks increasing by 300% since 2023 (CyberRisk Alliance 2025), comprehensive protection requires multi-layered redundancy. Implement these proven solutions:
3 Essential Backup Architectures
Local Backups (On-Premises Shield)
Media: External SSDs • NAS systems • LTO-9 tapes
Pros:
Near-instant recovery times
No bandwidth dependency
Cons:
Vulnerable to physical disasters
Limited scalability
Action: Store in fireproof safes • Maintain 3 copies
Cloud Backups (Off-Site Fortress)
Top Providers: Backblaze B2 • Google Cloud Storage • Azure Blob
Pros:
Geographic redundancy (auto-replication)
Military-grade encryption (AES-256 + TLS 1.3)
Ransomware rollback capabilities
Action: Enable versioning • Set 90-day retention policies
Hybrid Solution (The 3-2-1 Gold Standard)
Formula: 3 total copies • 2 media types • 1 off-site
Implementation:
NAS + Cloud + Air-gapped tape
Real-time sync + quarterly integrity checks
Action: Automate backups • Test restoration monthly
2025 Threat-Adjusted Protocols
AI-Enhanced Verification: Tools like Veeam v12 auto-detect corrupted backups
Immutable Storage: WORM-compliant clouds prevent malicious deletion
Zero-Trust Backup: Require MFA for all backup access
Encryption & Password Defense: 2025’s Data Fortress
In an era where data breaches cost $4.8M on average (IBM 2025 Report), robust encryption and password hygiene form your critical frontline defense. These aren’t just best practices—they’re regulatory requirements under GDPR/CCPA. Implement these enterprise-grade protections:
I. Military-Grade Encryption Implementation
Full Disk Encryption (FDE)
Scope: Encrypts entire drives (OS + files)
Thwart: Physical theft, unauthorized boot access
Action: Enable BitLocker (Win) / FileVault (Mac) pre-deployment
Granular File-Level Encryption
Use Case: Sensitive documents • Financial records • Media masters
Advantage: Selective protection without system slowdown
Action: Encrypt before cloud uploads or email attachments
Zero-Trust Encryption Tools
II. Password Integrity Protocols
Next-Gen Complexity Requirements
Formula: 14+ characters • 4 character types • No dictionary words
Evolution: Passphrases > passwords (“PurpleTiger$Eats_42Pizzas!”)
Action: Enforce via Azure AD/Okta policies
Absolute Password Uniqueness
Risk Mitigation: Breached credential scanning
Stat: 81% of breaches exploit reused passwords (Verizon DBIR 2025)
Action: Rotate high-privilege credentials monthly
Password Manager Mandates
Solutions: 1Password Teams • Keeper Enterprise • Bitwarden
Features:
Zero-knowledge architecture
Biometric 2FA integration
Emergency access protocols
Action: Provide company-wide licenses + training
2025 Defense Upgrades
Post-Quantum Encryption: Preparing for CRQC threats
Biometric Rotation: Monthly facial recognition re-scans
Behavioral Authentication: AI-powered anomaly detection
Patch Management & Security Training: 2025’s Cyber Resilience Duo
With 60% of breaches exploiting unpatched vulnerabilities (Ponemon 2025), proactive software maintenance and continuous education form your operational shield. These aren’t IT tasks – they’re revenue-protection strategies required by SOC 2 and ISO 27001.
I. Intelligent Patch Management Protocol
Vulnerability Neutralization
Priority: Critical CVEs within 24 hours
Thwart: Zero-day exploits • Ransomware delivery
Action: Establish CVSS-based patching SLAs
Performance-Driven Updates
Dual Benefit:
Security hardening (memory protection/Sandboxing)
Efficiency gains (reduced CPU overhead)
Action: Test patches in staging pre-deployment
Automated Update Ecosystems
Enterprise Tools:
ManageEngine Patch Manager Plus
Automox for cloud workloads
Action: Enable auto-updates for all Tier-1 assets
II. Security Education Framework
AI-Enhanced Phishing Defense
Modern Threats:
Deepfake voice scams
QR code phishing (Quishing)
Supply chain compromise
Action: Simulate quarterly spear-phishing tests
Zero-Trust Behavior Standards
Non-Negotiables:
SSL/TLS verification (padlock + cert checks)
Principle of least privilege access
Secure disposal of media
Action: Distribute encrypted security playbooks
Continuous Learning Cycles
Business Implementation:
Bi-monthly CISO briefings
Phish-prone % KPIs per department
VR threat-hunting simulations
Personal Implementation:
Quarterly security tool audits
Dark web monitoring alerts
MFA enforcement on all accounts
2025 Defense Upgrades
Predictive Patching: AI tools like TuxCare pre-apply virtual patches
Behavioral Biometrics: Detect compromised credentials via usage anomalies
Compliance Automation: Platforms like Drata auto-document training
Blockchain & Immutable Storage: 2025’s Anti-Tamper Armor for Media
As deepfake incidents surge 300% year-over-year (Forrester 2025), blockchain and WORM storage have become non-negotiable for media integrity. These technologies create unforgeable chains of custody and eliminate ransomware’s deadliest weapon – data deletion.
Core Technology Breakdown
Blockchain Verification
Function: Decentralized timestamped ledgers
Media Application:
Frame-by-frame content hashing
Smart contract royalties
NFT-based ownership certificates
Immutable WORM Storage
Function: Write Once, Read Many architectures
Enterprise Standards:
SEC/FINRA 17a-4 compliance
Cryptographic sealing
3 Media-Specific Security Advantages
Indisputable Ownership Proof
Blockchain-registered creation timestamps
Automated DMCA takedowns via smart contracts
Stat: Reduces copyright disputes by 78% (WIPO 2025)
Ransomware-Proof Backups
WORM-protected archives resist:
Encryption attacks
Admin credential compromise
“Zero-day” deletion exploits
Action: Store master files in AWS S3 Object Lock
Transparent Audit Trails
Permanent records of:
Access attempts
Edit proposals
Chain-of-custody transfers
Compliance: Meets GDPR Article 30 requirements
2025 Implementation Blueprint
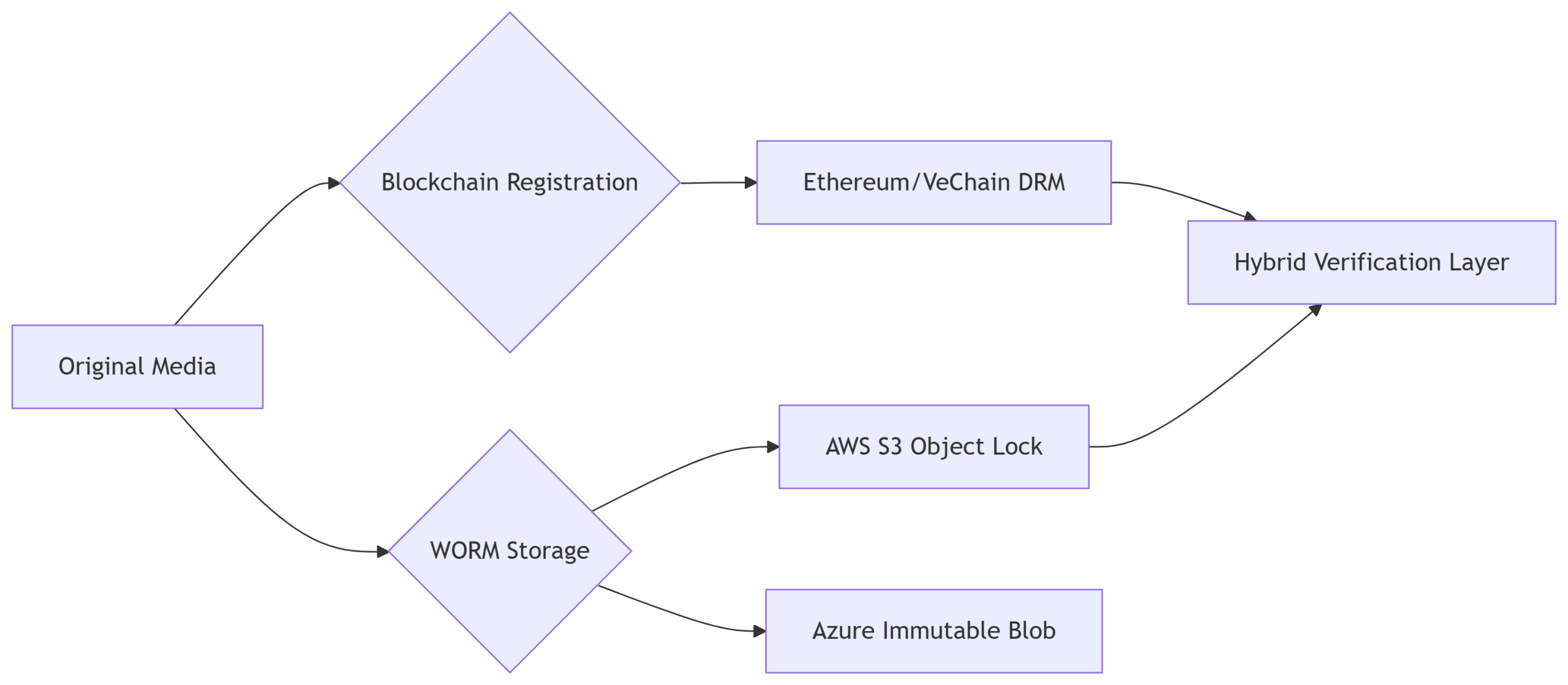
Actionable Deployment Steps
Content Registration
Hash new assets on Hedera Hashgraph
Embed NFT certificates in metadata
Immutable Archiving
Configure 7-year retention locks
Enable versioning + legal hold
Verification Integration
Use APIs from:
Truepic (authentication)
Zero-Trust Security: 2025’s Mandate for Media Asset Protection
With 74% of breaches involving privileged access abuse (Verizon DBIR 2025), Zero-Trust has shifted from “best practice” to non-negotiable for media enterprises. This “never trust, always verify” architecture reduces breach impact by 91% when fully implemented (Gartner).
Core Zero-Trust Framework
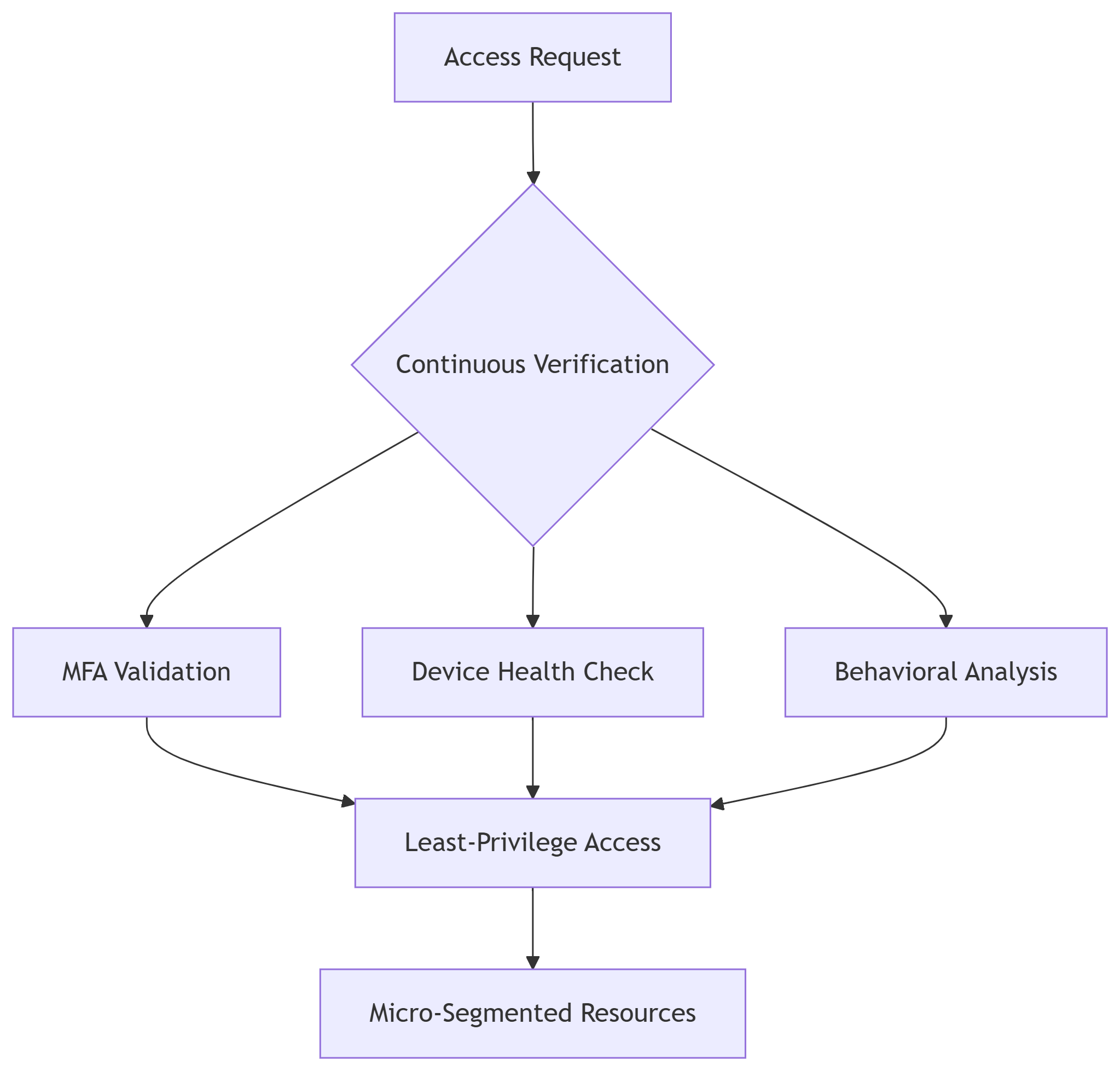
4 Battle-Tested Zero-Trust Pillars
Military-Grade MFA Enforcement
Requirements:
Phishing-resistant (FIDO2/WebAuthn)
Biometric fallbacks
Location-aware challenges
Action: Deploy Okta/Azure AD Conditional Access policies
Precision Privilege Management
Implementation:
JIT (Just-In-Time) access provisioning
15-minute permission windows for sensitive assets
Quarterly entitlement reviews
Stat: Reduces insider threat surface by 68%
AI-Powered Continuous Monitoring
Detection Capabilities:
Abnormal download patterns (4K RAW files)
Unauthorized cloud sync attempts
Suspicious rendering farm access
Action: Integrate Microsoft Sentinel/Securonix
Asset-Centric Microsegmentation
Media-Specific Architecture:
Isolate editing suites from corporate LAN
Air-gap archival storage
Encrypted pipelines for distribution
Compliance: Meets MPAA Content Security Standard
2025 Implementation Roadmap
Identity Foundation
Migrate to passwordless authentication
Implement privileged access workstations
Network Transformation
ZTNA replacing VPNs (Zscaler, Cloudflare)
SD-WAN with encrypted micro-tunnels
Asset Protection Layer
Tag media files with sensitivity metadata
Auto-classify using AI (Varonis, Titus)
Continuous Validation
Deploy UEBA for anomaly detection
Conduct bi-weekly breach simulations
In 2025, backup solutions are no longer optional—they’re your frontline defense against data loss, cyberattacks, and operational disruption. By implementing layered backups, zero-trust security, and advanced encryption, you create a resilient digital foundation that protects your business and your reputation.
Ready to upgrade your digital defenses?
Start by auditing your current backup strategy and take action on at least one improvement today. For expert guidance or a custom security plan,
contact our team now.
FAQs
What are the best ways to protect my digital media assets from cyberattacks?
Use multi-factor authentication (MFA)
Encrypt files during storage and transmission
Regularly back up data using local and cloud solutions
Implement zero-trust access controls
How can I securely share digital assets with external collaborators?
Use secure file-sharing platforms with encryption
Set role-based permissions and expiration dates on links
Avoid email attachments for sensitive files
Monitor access logs regularly
Why is zero-trust security important for digital asset protection?
It verifies every user and device before granting access
Limits insider threats by enforcing least privilege access
Continuously monitors for suspicious activity
Reduces risk of unauthorized data exposure
How does blockchain help in safeguarding media ownership rights?
Provides tamper-proof proof of ownership via timestamps
Creates transparent, immutable audit trails
Prevents unauthorized asset alteration or deletion
Supports digital rights management (DRM) solutions
When should I update my digital asset security protocols?
After any security breach or suspicious activity
When new software or hardware is introduced
At least quarterly for patch management and audits
Whenever compliance regulations change
What are common threats to digital media assets I should watch for?
Phishing and spear-phishing attacks
Ransomware encrypting your files
Unauthorized access from weak passwords
Deepfake and social engineering scams
How can I create an effective backup strategy for my digital assets?
Follow the 3-2-1 rule: 3 copies, 2 types of media, 1 off-site
Automate backups and test restoration regularly
Use immutable storage to prevent tampering
Encrypt backups and protect access with MFA
How do I implement multi-factor authentication for media asset security?
Choose MFA tools compatible with your systems (e.g., Azure AD, Okta)
Require MFA on all accounts with access to sensitive files
Educate users on MFA benefits and usage
Regularly review MFA logs for anomalies
What is the difference between encryption and watermarking for digital assets?
Encryption secures files by making data unreadable without keys
Watermarking embeds visible or invisible marks to prove ownership
Encryption protects data confidentiality; watermarking deters piracy
Can AI really detect threats to my digital assets better than traditional methods?
Yes, AI analyzes behavior patterns and anomalies in real time
It adapts to new threats faster than manual monitoring
AI can automate phishing detection and backup integrity checks
What legal protections should I consider for my digital media assets?
Register copyrights and trademarks for your content
Include IP clauses in employee and contractor agreements
Document ownership and access rights clearly
Consult an attorney for estate and asset protection planning
How does zero-trust architecture improve remote access security?
Continuously verifies user identity and device health
Limits access to only necessary resources
Monitors sessions for suspicious behavior
Reduces risk from compromised credentials or devices

