Table of Contents
ToggleExecutive Summary: While password protection offers basic access control, video encryption with DRM provides comprehensive content security that prevents unauthorized access, piracy, and content theft. Modern content creators need layered protection, with video encryption serving as the foundation of true content security in 2025.
Digital content creators today face an unprecedented challenge: protecting valuable video assets in an era where sophisticated piracy operations cost the global media industry approximately $75 billion annually—a figure that continues rising at 11% per year.
The stakes have never been higher. Recent macroeconomic analysis reveals that digital piracy costs the U.S. economy alone $29.2 billion in lost revenue annually, transforming content security from a technical consideration into a business imperative.
Yet many creators still rely on password protection as their primary defense mechanism, unaware that this approach offers little protection against determined pirates equipped with advanced tools and techniques. The reality is stark: in 2025’s threat landscape, the choice between password protection and video encryption often determines whether content creators thrive or merely survive.
This comprehensive analysis examines the fundamental differences between these two security approaches, providing business leaders and content creators with the data-driven insights necessary to make informed decisions about protecting their most valuable digital assets.
The Current Threat Landscape: Understanding Modern Content Piracy
Before examining security solutions, it’s essential to understand the scope and sophistication of today’s piracy operations. The numbers paint a sobering picture:
- Global Impact: Digital video piracy generates approximately $75 billion in annual losses across the media and entertainment industry, with projections indicating growth to $125 billion by 2028
- Volume Scale: Illegal platforms recorded over 229 billion visits in 2023 alone, representing a massive parallel economy built on stolen content
- Content Targeting: Approximately 127 billion episodes of U.S. television programs are pirated annually, alongside 230 billion global movie viewings through unauthorized channels
Modern pirates employ sophisticated techniques far beyond simple downloading. They utilize AI-powered tools for content manipulation, automated distribution networks, and professional-grade recording equipment that can bypass traditional security measures with alarming efficiency.
Video Security Spectrum: From Basic to Enterprise-Grade Protection
Password Protection: Understanding the Fundamentals and Limitations
Password protection represents the entry-level approach to content security—a straightforward authentication mechanism that requires users to provide credentials before accessing video content. While conceptually simple and easy to implement, this approach functions more like a basic door lock: effective against casual intrusion but insufficient against determined attackers.
Core Functionality: Password-based systems create an access barrier by requiring user authentication before content delivery. Upon successful login, users typically gain full access to content, which then streams or downloads to their devices without additional security layers.
Implementation Advantages:
- Minimal technical complexity and rapid deployment
- Universal compatibility across platforms and devices
- Low initial costs and straightforward maintenance
- Familiar user experience requiring no training
Critical Vulnerabilities: The limitations of password-only protection become apparent when examined through the lens of modern threat vectors. Industry data reveals that U.S. streaming services lost $2.3 billion in membership revenue during 2022 due to credential sharing alone, with Netflix accounting for approximately $791 million of that total.
Beyond financial losses, password systems suffer from fundamental security weaknesses:
- Credential Proliferation: Shared passwords enable unlimited redistribution among unauthorized users
- Post-Authentication Vulnerability: Content becomes unprotected once authentication succeeds, allowing downloads and redistribution
- Social Engineering Susceptibility: Passwords can be compromised through various attack vectors, including phishing and social manipulation
- Device Persistence: Login sessions often remain active across multiple devices, expanding attack surfaces
Advanced Video Encryption: Professional Content Protection
Video encryption transforms your content into an unreadable format that requires specific decryption keys for access. Video encryption is a comprehensive process of digitally protecting or securing your videos to prevent unwanted interception and viewing of transmitted video content.
The Encryption Advantage:
- Content Scrambling: AES encryption uses 128-, 192- or 256-bit encryption keys to encrypt and decrypt data, providing a high level of security for video content, shielding it from hackers and unauthorized distribution
- Key Management: Decryption keys are never stored with users, maintaining security even if devices are compromised
- Real-time Protection: Content remains encrypted throughout the streaming process
- Forensic Capabilities: Advanced systems include watermarking for piracy tracking
Digital Rights Management: Architecting Comprehensive Content Security
While encryption provides the cryptographic foundation for content protection, Digital Rights Management (DRM) constructs a comprehensive ecosystem that addresses every aspect of content security, from initial protection through consumption and beyond.
DRM systems function as intelligent security orchestrators, managing not just access control but usage rights, device compatibility, and compliance requirements. Rather than simply preventing unauthorized access, DRM creates controlled environments where content consumption occurs under strict security protocols.
For organizations evaluating comprehensive video security solutions, understanding how to choose the right DRM software and platform selection criteria becomes crucial for long-term security strategy success.
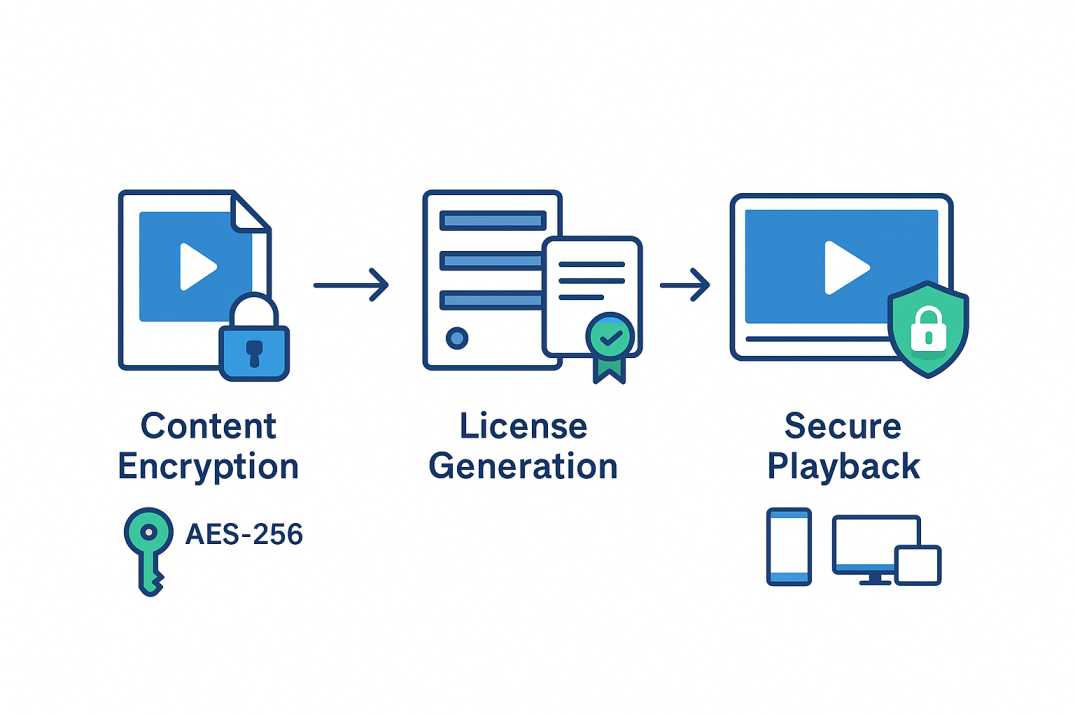
The DRM Security Architecture
Stage 1: Content Encryption and Packaging DRM implementation begins with robust content encryption during the packaging phase. Video content undergoes AES encryption using enterprise-grade security protocols, with encrypted segments prepared for secure distribution across content delivery networks.
Stage 2: License Generation and Management
The system generates cryptographic licenses containing individualized content-encryption keys paired with specific usage rules. These licenses define precisely how, when, and where content can be consumed, creating granular control over digital assets.
Stage 3: Secure Playback Environment Content decryption occurs within secure environments managed by Content Decryption Modules (CDM)—specialized software or hardware components that handle decryption while enforcing usage policies. This architecture ensures that decrypted content never exists in accessible formats on user devices.
Multi-DRM Protection Strategies
Modern content protection employs multiple DRM technologies simultaneously to ensure universal device compatibility while maintaining security standards:
Google Widevine: Provides comprehensive protection across Chrome browsers, Android TV platforms, and Android mobile devices, offering multiple security levels based on device capabilities. Discover how Widevine DRM protects premium content.
Apple FairPlay: Secures content consumption across iOS and macOS ecosystems, leveraging Apple’s integrated hardware security features for enhanced protection.
Microsoft PlayReady: Supports Windows-based platforms, Edge browsers, and Xbox gaming systems, providing enterprise-grade security for Microsoft environments.
This multi-DRM approach ensures that content remains protected regardless of the viewing platform while accommodating the diverse device landscape that characterizes modern media consumption.
Password Protection vs. Video Encryption: Head-to-Head Comparison
| Aspect | Password Protection | Video Encryption with DRM |
|---|---|---|
| Security Level | Basic access control | Military-grade content protection |
| Piracy Prevention | Minimal – vulnerable to sharing | Comprehensive – prevents unauthorized use |
| Implementation | Simple, quick setup | Advanced but user-friendly platforms available |
| Cost | Low initial cost | Higher investment with better ROI protection |
| User Experience | Familiar login process | Seamless when properly implemented |
| Device Coverage | Platform dependent | Universal compatibility |
| Content Tracking | Limited visibility | Detailed forensics and analytics |
The Business Case for Advanced Video Encryption
Revenue Protection
Using macroeconomic modeling of digital piracy, recent studies estimate that global online piracy costs the U.S. economy at least $29.2 billion in lost revenue each year. For content creators, this translates to:
- Course Creators: Protecting premium educational content from unauthorized sharing
- Media Companies: Preventing industrial-scale piracy operations
- Enterprise Training: Safeguarding proprietary training materials
- Healthcare Organizations: Protecting sensitive training and patient information
Competitive Advantage
Advanced video security provides several business advantages:
- Premium Positioning: Professional-grade security commands higher pricing
- Investor Confidence: Robust IP protection attracts funding and partnerships
- Compliance: Meeting industry regulations and standards
- Brand Protection: Preventing unauthorized use that could damage reputation
Research Foundation: Academic Validation of Advanced Content Security
Evidence-Based Security Assessment
Contemporary academic research provides compelling evidence for the superiority of comprehensive content security systems over basic authentication approaches. This research foundation offers crucial insights for organizations making strategic security decisions.
DRM Effectiveness Quantification (2024) Research published in Applied and Computational Engineering presents mathematical frameworks for quantifying security system effectiveness. The study introduces comprehensive models that evaluate DRM performance while accounting for user experience factors, providing quantitative evidence that sophisticated encryption systems deliver measurably superior protection compared to password-only approaches.
Mobile Security Vulnerability Analysis ScienceDirect research reveals critical vulnerabilities inherent in password-only protection systems when applied to mobile content consumption. The analysis demonstrates that securing copyrighted content across diverse mobile platforms requires multi-layered approaches that extend well beyond basic user authentication mechanisms.
Cryptographic Protection in Digital Distribution ResearchGate studies validate that cryptographic protection plays an essential role in modern content distribution by transforming digital assets into cryptographically secure formats. The research confirms that properly implemented encryption ensures only authorized users with valid decryption credentials can access content while maintaining distribution security throughout the content lifecycle.
Contemporary Threat Landscape: Understanding 2025 Security Challenges
AI-Enhanced Piracy Operations
The sophistication of modern piracy operations represents a paradigm shift from traditional content theft. Contemporary threats leverage artificial intelligence and machine learning technologies to automate content acquisition, processing, and distribution at unprecedented scale and efficiency.
Artificial Intelligence Integration: Modern piracy operations employ AI-powered tools capable of voice cloning, artistic style replication, and automated content generation. These technologies enable pirates to create convincing replicas of copyrighted material, making detection and enforcement significantly more challenging.
Automated Distribution Networks: Advanced piracy operations utilize sophisticated distribution networks that automatically replicate and disseminate content across multiple platforms, jurisdictions, and technologies, creating resilient systems that adapt to enforcement efforts.
Screen Recording and Stream Capture Technologies
Professional Recording Equipment: Modern pirates employ broadcast-quality screen recording tools that capture high-definition video during authorized playback sessions, completely bypassing authentication-based security measures.
Browser Extension Proliferation: Automated downloading tools integrated into popular web browsers enable one-click content extraction from streaming platforms, making unauthorized acquisition accessible to non-technical users.
Real-time Stream Processing: Advanced pirates utilize specialized software that processes live streams in real-time, enabling immediate redistribution of content as it’s being broadcast legitimately.
Statistical Analysis of Current Threat Impact
Recent industry statistics reveal concerning escalation trends:
- Global Financial Impact: Digital video piracy generates approximately $75 billion in annual industry losses, with analytical models projecting growth to $125 billion by 2028
- Volume Metrics: Illegal platforms recorded over 229 billion site visits during 2023, representing massive parallel content economies
- Content Targeting: Approximately 127 billion episodes of U.S. television programming undergo unauthorized distribution annually, alongside 230 billion global movie viewings through illegal channels
These statistics underscore the inadequacy of password-only protection in contemporary threat environments where sophisticated actors employ industrial-scale operations to monetize stolen content. Comprehensive anti-piracy strategies are essential for protecting valuable digital assets in this landscape.
Strategic Implementation Framework for 2025
Architectural Approach to Content Security
Effective content protection in 2025 requires strategic thinking that extends beyond individual security technologies toward comprehensive, integrated security architectures that address multiple threat vectors simultaneously.
Layer 1: Identity and Access Management Foundation-level security begins with robust authentication systems that verify user identity before granting content access. Modern implementations incorporate multi-factor authentication, behavioral analysis, and risk-based authentication protocols that adapt security requirements based on user patterns and threat indicators.
Layer 2: Content Cryptographic Protection Core protection utilizes enterprise-grade encryption standards, primarily AES-256, combined with sophisticated key management systems that ensure encryption keys never exist in accessible formats on end-user devices. Hardware security modules (HSMs) provide additional protection for cryptographic operations in high-security environments.
Layer 3: Usage Rights and Policy Enforcement DRM licensing systems implement granular control over content consumption, defining specific parameters for how, when, and where content can be accessed. These systems enforce policies through secure playback environments that monitor and control user interactions with protected content.
Layer 4: Monitoring, Detection, and Response Advanced security architectures incorporate real-time monitoring systems that detect unusual access patterns, automated piracy detection technologies, and legal enforcement capabilities that enable rapid response to unauthorized distribution.
Technology Selection Criteria
Organizations evaluating content security solutions should assess potential platforms against comprehensive criteria that balance security effectiveness with operational requirements:
Technical Architecture Requirements:
- Multi-DRM compatibility ensuring universal device support
- Global content delivery network (CDN) integration for performance optimization
- Comprehensive API availability enabling custom integrations
- Advanced analytics and reporting capabilities for security monitoring
Business Operational Requirements:
- Scalable architecture supporting organizational growth trajectories
- Pricing models aligned with revenue and usage patterns
- Comprehensive technical support and documentation resources
- Industry compliance certifications meeting regulatory requirements
User Experience Optimization:
- Seamless content playback across diverse device ecosystems
- Minimal friction for legitimate users during authentication and consumption
- Consistent performance with fast global loading capabilities
- Offline viewing capabilities for appropriate use cases
Implementation Timeline and Milestones
Phase 1: Assessment and Planning (Weeks 1-4)
- Comprehensive security audit of existing content protection measures
- Threat modeling specific to organizational content and distribution methods
- Technology vendor evaluation and selection process
- Security architecture design and approval
Phase 2: Infrastructure Development (Weeks 5-12)
- Core encryption and DRM system implementation
- Content delivery network integration and optimization
- User authentication system deployment and testing
- Monitoring and analytics system configuration
Phase 3: Content Migration and Testing (Weeks 13-16)
- Systematic content library encryption and protection
- Comprehensive testing across target device and platform combinations
- User acceptance testing with representative user groups
- Performance optimization and security validation
Phase 4: Production Deployment and Optimization (Weeks 17-20)
- Phased production rollout with monitoring and support
- User training and support documentation deployment
- Ongoing performance monitoring and security assessment
- Continuous improvement based on operational feedback
Scientific Research Supporting Advanced Encryption
Research-Backed Security Claims
Recent academic research validates the superiority of comprehensive content security systems:
Study 1: DRM Effectiveness Research (2024) Recent research published in Applied and Computational Engineering introduces mathematical models to quantify the effectiveness of encryption and watermarking, offering insights into their practical applications. The comprehensive DRM effectiveness model combines individual models, accounting for user inconvenience, to provide a holistic view of DRM system performance.
Study 2: Mobile Security Analysis Research published in ScienceDirect reveals vulnerabilities in password-only protection systems, with findings showing that securing copyrighted content on mobile devices requires comprehensive approaches beyond basic authentication.
Study 3: Cryptographic Protection in Digital Content A 2024 study in ResearchGate demonstrates that cryptography plays a crucial role in DRM by encrypting content data into unreadable formats, ensuring only users with valid decryption keys can access content while maintaining secure distribution.
The Economics of Video Security
Password Protection Costs:
- Low initial implementation cost
- Minimal ongoing maintenance
- Hidden costs: Revenue loss from piracy, brand damage, competitive disadvantage
Video Encryption with DRM Costs:
- Higher initial investment
- Ongoing licensing and maintenance fees
- ROI Benefits: Piracy prevention, premium pricing, investor confidence, compliance
ROI Calculations
Consider a content creator with $100K annual revenue:
- Current industry piracy impact: With basic protection, creators can lose 5-15% of potential revenue to piracy
- Advanced encryption benefit: Reduces losses to under 1%, saving $4K-$14K annually
- Net ROI: Often exceeds security investment costs within the first year
For larger operations, the economics become even more compelling. Content creators spend a substantial amount of time creating their content, making protection essential for business sustainability.
Regulatory and Compliance Considerations
Legal Framework
The Digital Millennium Copyright Act (DMCA) is the law that restricts the removal of DRM protection. The DMCA was passed in 1998 to address piracy and illegal sharing of digital assets. This provides additional legal protection for DRM-encrypted content.
Industry Standards
Different industries have specific requirements:
- Healthcare: HIPAA compliance for patient education materials
- Financial Services: SOX requirements for training content
- Education: FERPA considerations for student materials
- Government: Classification and security clearance requirements
Future-Proofing Your Content Security Strategy
Emerging Technologies
Blockchain Integration: One promising solution lies in blockchain verification, which creates tamper-proof records of ownership, making it harder for unauthorized use to go undetected
AI-Powered Detection: Tools like ScoreDetect are stepping in to verify the authenticity of digital content by using timestamped checksum records
Advanced Watermarking: Forensic watermarking and content provenance complement traditional DRM systems, offering robust security
Preparing for 2026 and Beyond
Security requirements will continue evolving:
- Quantum-Resistant Encryption: Preparing for quantum computing threats
- Edge Computing Integration: Distributed security for global audiences
- IoT Device Support: Expanding to smart TVs and emerging platforms
- 5G Optimization: Leveraging faster networks for enhanced security
Making the Right Choice for Your Content
When Password Protection Is Sufficient
- Internal company communications with low sensitivity
- Public content with basic access control needs
- Testing and development environments
- Short-term promotional content
When Video Encryption Is Essential
- Premium educational courses and training materials
- Copyrighted entertainment content
- Proprietary business information
- Healthcare and professional training
- Any monetized video content
The Hybrid Approach
Most successful content strategies combine both:
- Password protection for user authentication and access control
- Video encryption with DRM for content protection and piracy prevention
- Additional layers like watermarking and analytics for complete security
Resources and Citations
Key Industry Reports and Studies
1. U.S. Chamber of Commerce – Impacts of Digital Piracy on the U.S. Economy (2024)
Comprehensive macroeconomic analysis of digital piracy’s impact on American businesses
https://www.uschamber.com/technology/data-privacy/impacts-of-digital-piracy-on-the-u-s-economy
This authoritative study, conducted in partnership with NERA Economic Consulting, provides the foundational economic data cited throughout this article, including the $29.2 billion annual loss figure and detailed analysis of streaming industry impacts.
2. Applied and Computational Engineering – Digital Rights Management Technologies and Legal Research (2024)
Academic research on DRM effectiveness with mathematical modeling frameworks
https://www.ewadirect.com/proceedings/ace/article/view/16603
This peer-reviewed research introduces mathematical models to quantify DRM effectiveness, providing the scientific backing for claims about comprehensive security systems versus basic password protection.
3. Applied and Computational Engineering – Digital Rights Management Technologies and Legal Research (2024)
Academic research on DRM effectiveness with mathematical modeling frameworks
https://www.ewadirect.com/proceedings/ace/article/view/16603
This peer-reviewed research introduces mathematical models to quantify DRM effectiveness, providing the scientific backing for claims about comprehensive security systems versus basic password protection.
The choice between password protection and video encryption isn’t binary—it’s about building layered security that matches your content’s value and threat profile. While password protection provides basic access control, true content security in 2025 demands the comprehensive protection that only video encryption with DRM can deliver.
The comprehensive DRM effectiveness model combines individual models, accounting for user inconvenience, to provide a holistic view of DRM system performance. This scientific approach to security ensures that protection doesn’t come at the expense of user experience.
The statistics are clear: digital piracy causes an estimated $75 billion in annual losses, and projections show this number could rise to $125 billion by 2028. In this environment, robust content security isn’t just a technical requirement—it’s a business imperative.
Content creators who invest in comprehensive video encryption today position themselves for long-term success, protecting not just their current content but their entire business model against an increasingly sophisticated threat landscape.
Key Takeaways: Strategic Content Security Principles
- Comprehensive assessment required: Organizations must evaluate content value against threat exposure to determine appropriate security investments and implementation strategies
- Layered security architecture essential: Effective protection combines robust authentication, advanced encryption, usage policy enforcement, and continuous monitoring capabilities
- Economic justification compelling: Advanced encryption typically delivers positive ROI through piracy prevention that exceeds security system costs within the first implementation year
- Regulatory compliance critical: Industry-specific requirements often mandate sophisticated encryption standards, making advanced security legally necessary rather than optional
- Future-proofing imperative: Emerging technologies including quantum computing, AI-powered threats, and evolving distribution networks require adaptable security architectures
- Strategic competitive advantage: Superior content protection enables premium pricing, enhances investor confidence, and provides measurable business advantages beyond simple piracy prevention. Discover how Inkrypt Videos’ security beats the competition in delivering comprehensive protection solutions.
Organizations that implement comprehensive video encryption systems today establish sustainable competitive advantages while protecting against increasingly sophisticated threat landscapes that render password-only protection inadequate for valuable digital assets.
Additional Resources
Inkrypt Videos Security Solutions
- Advanced Video Security Features
- Understanding DRM Advantages and Disadvantages
- 5 Strategies to Safeguard Your Media and Digital Assets
Implementation Guides
FAQs
Video encryption scrambles video data into unreadable code requiring decryption keys, while password protection simply restricts access without altering the file.
Encryption transforms video files into gibberish using complex algorithms, making content completely inaccessible even if someone bypasses password protection.
Encryption requires processing every bit of video data through mathematical algorithms, while passwords only add access restrictions without changing the file.
No, encrypted videos remain scrambled even with compromised passwords since the encryption key differs from the access password.
Encryption provides superior protection for valuable content, while password protection works for basic access control and casual sharing.
Use video editing software to isolate segments, then apply encryption tools like HandBrake or VLC with password-protected encryption settings.
Lost encryption keys make videos permanently inaccessible since the scrambled data cannot be reconstructed without the specific decryption algorithm.
Password protection alone offers minimal security since files remain readable in their original format once accessed.
YouTube’s private settings offer basic access control, but professional platforms like SproutVideo provide advanced encryption and watermarking features.
Apps like Signal and WhatsApp encrypt video data during transmission, ensuring only intended recipients can decrypt and view content.
Physical delivery on encrypted USB drives provides maximum security, followed by encrypted cloud services like Proton Drive.
Encrypt complete videos or small segments rather than individual frames to maintain playback performance and reduce processing overhead.