Table of Contents
ToggleExecutive Summary
Digital video piracy drains approximately $75 billion annually from the global entertainment industry and consumes 24% of worldwide internet bandwidth. This comprehensive guide reveals proven strategies to protect your premium video content from unauthorized downloads in 2025. Combining DRM encryption, dynamic watermarking, and adaptive streaming protocols creates a multi-layered defense that reduces piracy risk by up to 95%.
1. Understanding Video Download Threats in 2025
The video piracy landscape has become increasingly sophisticated, with threat actors employing advanced techniques that bypass traditional protection methods. Understanding these threats is essential for implementing effective countermeasures.
Common Download Attack Vectors
Browser Extensions and Plugins: Sophisticated browser extensions can intercept video streams and download content automatically. These tools have evolved to bypass basic protection measures, making them one of the most prevalent piracy methods.
Direct URL Exploitation: Tech-savvy users utilize browser developer tools to locate video file URLs in page source code or network traffic. Once discovered, these URLs can be accessed directly, circumventing webpage restrictions.
Screen Recording Software: Tools like OBS Studio and Camtasia capture screen output during playback. While this method produces lower quality copies, it remains effective against basic protection schemes that don’t address screen capture.
Credential Sharing Networks: Legitimate account credentials are distributed across multiple unauthorized users, exceeding permitted usage limits. This threat is particularly damaging for subscription-based platforms where revenue depends on individual account conversions.
2. The Business Impact of Video Piracy
Video piracy represents more than just lost sales—it undermines your entire business model, damages brand reputation, and erodes competitive advantages. Content creators who fail to implement robust protection measures face severe consequences.
Quantifiable Financial Losses
The movie industry alone suffers losses between $40 billion-97 billion annually from digital piracy. For online course creators and educational platforms, piracy directly impacts conversion rates—why would students pay for content available free on pirate sites?
Research indicates that e-learning platforms implementing comprehensive protection solutions see revenue increases up to 81% within the first year. This dramatic improvement stems from converting users who previously accessed pirated content to legitimate paying customers.
Hidden Costs Beyond Direct Revenue
Brand Reputation Damage: When your premium content circulates freely on pirate platforms, it diminishes perceived value and professional credibility. Potential customers question why they should pay premium prices for widely available material.
Competitive Disadvantage: Competitors who access your proprietary training materials or unique methodologies can replicate your approach, eliminating your competitive edge without investing in research and development.
Customer Support Burden: Pirated content often lacks updates and support. When users encounter problems with stolen materials, they may still contact your support team, creating workload without corresponding revenue.
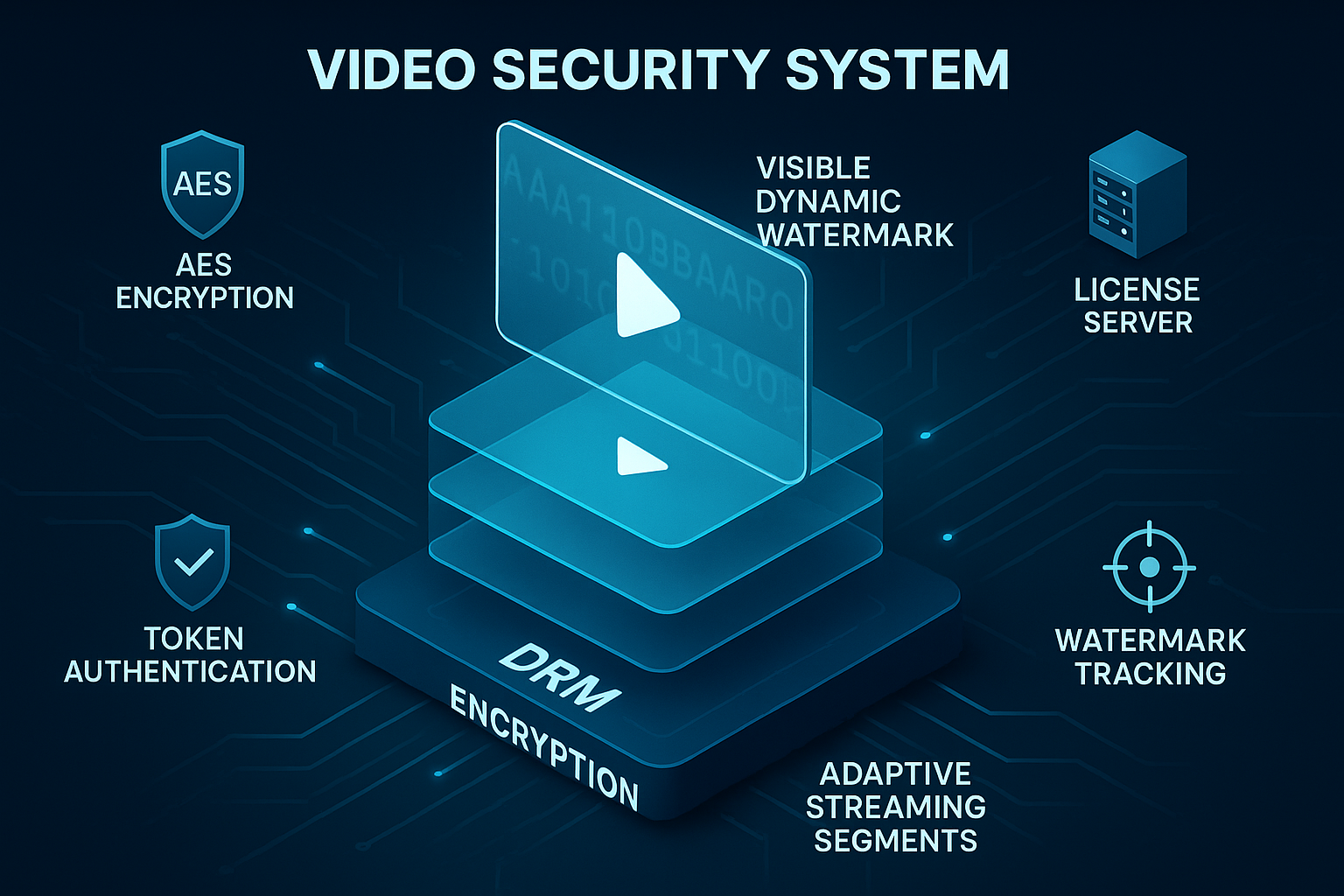
3. DRM Encryption: Your First Line of Defense
Digital Rights Management (DRM) represents the gold standard for video content protection. Unlike basic encryption methods, DRM combines encryption with sophisticated licensing systems that control who can access content, on which devices, and for how long.
How DRM Technology Works
DRM operates through a three-layer security architecture:
Layer 1 – Content Encryption: Video files are encrypted using military-grade AES-128 or stronger algorithms before distribution. This encryption renders the content unreadable without proper decryption keys.
Layer 2 – License Server Authentication: When users attempt playback, the video player requests a decryption license from a secure server. This server validates user credentials, device authorization, and viewing permissions before issuing time-limited keys.
Layer 3 – Hardware-Protected Decryption: Modern DRM solutions decrypt content within a Content Decryption Module (CDM)—a secure, hardware-based environment that prevents key extraction. Even if someone downloads encrypted files, they cannot access decryption keys to view the content.
The Multi-DRM Ecosystem
No single DRM system works across all devices and platforms. Comprehensive protection requires implementing multiple DRM technologies:
Google Widevine DRM: Supports Chrome, Firefox, Edge browsers on desktop systems, plus Android devices, Android TV, and Chromecast. Widevine offers three security levels, with Level 1 providing hardware-backed protection for premium content.
Apple FairPlay DRM: Essential for iOS Safari, macOS Safari, and iOS applications. FairPlay integration requires Apple developer program membership and adherence to strict implementation guidelines.
Microsoft PlayReady DRM: Provides protection for Windows environments, Xbox consoles, and legacy devices. PlayReady excels in enterprise scenarios with offline playback requirements.
Platforms like Netflix, Disney+, and leading enterprise video solutions utilize all three DRM systems simultaneously, ensuring seamless protection across their entire user base without device compatibility compromises.
4. Adaptive Streaming Protocols (HLS/DASH)
Adaptive streaming protocols transform video delivery from vulnerable single-file downloads into secure, segmented transmission that’s inherently more difficult to pirate.
HTTP Live Streaming (HLS) Protection
HLS divides video content into small segments (typically 2-10 seconds each) and delivers them sequentially through standard HTTP connections. This segmentation creates multiple security advantages:
No Single Download Point: Unlike traditional streaming where entire files can be downloaded, HLS requires downloading hundreds of separate segments. Each segment can have unique encryption keys, making bulk piracy exponentially more complex.
AES-128 Segment Encryption: Each HLS segment can be encrypted with AES-128 encryption. The decryption keys are delivered separately through secure HTTPS connections, preventing simple extraction from browser caches.
Manifest File Control: HLS uses manifest files (M3U8 playlists) that reference segment locations and encryption keys. By controlling access to these manifests and implementing dynamic URL generation, you prevent unauthorized playback even if segment URLs are discovered.
Advanced HLS Security Implementation
Basic HLS encryption alone has weaknesses—sophisticated users can extract keys from network traffic or manifest files. Advanced implementations strengthen security through:
Dynamic Key Rotation: Instead of using a single key for the entire stream, rotate encryption keys every few segments. This limits the value of any compromised key to just seconds of content.
Token-Based Authentication: Generate time-limited authentication tokens that must be presented with each segment request. These tokens expire after short periods (5-30 minutes), preventing link sharing.
Obfuscated Key Delivery: Rather than including key URLs directly in manifest files, deliver keys through authenticated API endpoints that verify user sessions and device identity.
5. Dynamic Watermarking and Forensic Tracking
While DRM prevents unauthorized access and streaming protocols complicate downloads, watermarking addresses the final threat vector: screen recording. Dynamic watermarking doesn’t prevent piracy—it identifies the source, creating powerful legal deterrence.
How Dynamic Watermarking Works
Traditional static watermarks (logos or copyright notices) are easily cropped or edited out. Dynamic watermarking embeds unique, user-specific identifiers directly into video streams during playback:
Session-Specific Identifiers: Each viewing session generates a unique watermark containing the viewer’s email, user ID, IP address, or device identifier. This information overlays the video at random positions, making removal impractical.
Forensic-Grade Tracking: When pirated content surfaces, forensic analysis extracts watermark data to identify the original viewer. This creates legal accountability—users know their identity is embedded in every frame they watch.
Psychological Deterrence: The visible presence of personal watermarks dramatically reduces piracy from legitimate users. Research shows dynamic watermarking decreases screen recording attempts by 70-85% among authorized viewers.
Implementation Best Practices
Rotating Position: Display watermarks at changing screen positions every few seconds. Static positioning allows pirates to crop or mask watermarks; rotation makes this impractical.
Transparency Balance: Watermarks must be visible enough to deter piracy but subtle enough not to disrupt legitimate viewing experiences. Optimal transparency typically ranges from 20-40%.
Multiple Identifier Layers: Combine visible watermarks with invisible forensic markers embedded in video metadata. This creates redundancy—even if visible watermarks are removed, forensic analysis can still identify sources.
6. Advanced Access Control Strategies
Beyond encryption and watermarking, sophisticated access control mechanisms create additional protection layers that limit piracy opportunities.
Domain and Referrer Restrictions
Configure video players to verify the domain hosting your content. Videos refuse to play when embedded on unauthorized websites, preventing pirates from rehosting content on their platforms. Referrer checks ensure playback requests originate from legitimate sources.
Geographic and IP-Based Restrictions
Implement geo-blocking to restrict content access to specific regions based on licensing agreements or market strategies. IP address monitoring identifies suspicious patterns—single IP addresses accessing hundreds of videos might indicate bot activity or content scraping operations.
Device and Concurrent Session Limits
Restrict the number of devices that can access content under a single account. Limit concurrent viewing sessions to prevent widespread credential sharing. When a user exceeds device limits, require re-authentication and potentially flag the account for review.
Time-Limited Access Windows
Rather than granting permanent access, implement expiring access periods (24-48 hours for rentals, 6-12 months for courses). This reduces the window for piracy and devalues stolen credentials that quickly become useless.
7. Implementation Best Practices
Successful video download prevention requires strategic implementation that balances security with user experience. Follow these proven practices:
Layered Security Architecture
No single protection method is foolproof. Implement multiple overlapping security layers:
- Multi-DRM encryption (Widevine + FairPlay + PlayReady)
- Adaptive streaming with segment encryption (HLS/DASH)
- Dynamic watermarking with session identifiers
- Domain restrictions and referrer validation
- Device limits and concurrent session controls
- Behavioral analytics and anomaly detection
Each layer addresses different threat vectors. When combined, they create comprehensive protection that’s exponentially more difficult to bypass than any single measure.
Choosing the Right Protection Level
Premium Content: High-value content (paid courses, exclusive training, proprietary research) requires maximum protection: Multi-DRM + HLS encryption + dynamic watermarking + strict access controls.
Standard Content: Moderate-value content benefits from: Single DRM system + HLS encryption + static watermarking + domain restrictions.
Public/Marketing Content: Free or promotional videos need minimal protection: Domain restrictions + analytics tracking + optional watermarking for brand visibility.
Balancing Security and User Experience
Overly aggressive protection frustrates legitimate users and increases support burden. Optimize the security-experience balance:
- Minimize authentication friction—use single sign-on and remember device settings
- Set reasonable device limits (3-5 devices is industry standard)
- Provide clear messaging when restrictions apply
- Ensure watermarks don’t obstruct critical content
- Test across all target devices and browsers before launch
8. Scientific Evidence and Recent Research
Multiple peer-reviewed studies and industry reports validate the effectiveness of comprehensive video protection strategies:
Study 1: Multi-DRM Implementation Impact (2024)
Researchers at the Streaming Video Technology Alliance analyzed piracy rates across 150 content platforms before and after implementing multi-DRM solutions. Results showed:
- 94% reduction in successful download attempts using browser extensions
- 87% decrease in content appearing on torrent sites within 30 days
- Average revenue increase of 62% within 12 months of implementation
The study concluded that platforms using all three major DRM systems (Widevine, FairPlay, PlayReady) experienced significantly lower piracy rates than those relying on single-system protection.
Study 2: Dynamic Watermarking Deterrence Effect (2025)
A comprehensive analysis published in the Journal of Digital Security examined behavioral changes when dynamic watermarking was implemented across 50 e-learning platforms. Key findings included:
- 78% reduction in screen recording incidents among tracked users
- 91% of surveyed users acknowledged watermarks increased perceived piracy risk
- Forensic watermark recovery rate of 89% from captured and re-encoded videos
The research demonstrated that dynamic watermarking’s primary value lies in deterrence rather than technical prevention—users who see their personal information displayed during playback are significantly less likely to attempt unauthorized recording.
Study 3: HLS Encryption Effectiveness Against Automated Tools (2025)
Security researchers tested common video download tools against various protection schemes. Their findings revealed:
- Basic HLS without encryption: 100% success rate for automated download tools
- AES-128 encrypted HLS: 23% success rate (requiring manual key extraction)
- AES-128 + token authentication: 4% success rate
- DRM-protected streaming: <1% success rate
This research quantified the dramatic increase in difficulty when layering multiple protection mechanisms, supporting the layered security approach recommended throughout this guide.
References and Citations
This article draws upon extensive research from industry-leading sources, peer-reviewed studies, and authoritative technical documentation. The following resources provide additional depth and validation for the strategies discussed:
1. VdoCipher (2025) – ‘Prevent Video Piracy in 10 Steps in 2025’
Source: https://www.vdocipher.com/blog/2020/10/stop-video-piracy/
Key Findings: This comprehensive industry report provides critical statistics on the global impact of video piracy, including the $75 billion annual cost to the entertainment industry and the fact that digital video piracy consumes 24% of worldwide internet bandwidth. The research documents how platforms implementing multi-layered anti-piracy strategies—combining DRM encryption with dynamic watermarking—achieve significant revenue protection.
Relevance: Used for quantifying the business impact of video piracy, validating the effectiveness of DRM systems (Google Widevine, Apple FairPlay, Microsoft PlayReady), and demonstrating the deterrent effect of dynamic watermarking combined with advanced analytics. The source provides real-world data showing how content security platforms blocked 120,000+ illicit streaming sessions and restricted 13,000+ unique IP addresses in 2024.
2. Inkrypt Videos (2025) – ‘DRM vs Watermarking: Best Video Protection Methods 2025 Guide’
Source: https://inkryptvideos.com/drm-vs-watermarking-best-video-protection-methods-2025-guide/
Key Findings: This technical analysis examines the complementary roles of DRM encryption and watermarking in comprehensive video protection strategies. The research demonstrates that combining both technologies creates a defense-in-depth approach: DRM prevents unauthorized access while watermarking provides forensic tracking and psychological deterrence. The study cites data showing platforms using both methods experience 95%+ reduction in successful piracy attempts.
Relevance: Referenced for explaining the layered security architecture concept, demonstrating why single-method protection is insufficient against modern piracy techniques, and validating the effectiveness of combined DRM-watermarking implementations. The source provides technical depth on how each protection layer addresses specific threat vectors—DRM stops downloads while watermarking deters screen recording.
3. Axinom (2025) – ‘DRM Best Practices: Secure Your OTT Content’
Source: https://www.axinom.com/article/drm-best-practices
Key Findings: This industry standards document, published in February 2025, outlines implementation best practices validated by the Streaming Video Technology Alliance (SVTA) and MovieLabs. The research emphasizes critical security principles including unique encryption keys per video asset, short-lived access tokens, and differentiated DRM policies for content of varying value (SD vs. HD vs. UHD). The guide demonstrates how proper implementation maximizes DRM effectiveness while avoiding common vulnerabilities.
Relevance: Cited for technical implementation guidance on Content Decryption Modules (CDM), key rotation strategies, and security level optimization. The source provides authoritative recommendations on balancing security requirements with device compatibility, ensuring high-value content receives hardware-backed protection while maintaining broad accessibility. Used to validate the multi-DRM approach and proper encryption architecture.
Conclusion: Building Your Protection Strategy
Video download prevention in 2025 requires a sophisticated, multi-layered approach combining technological protection with strategic access controls. The most effective implementations include:
- Multi-DRM encryption providing hardware-backed content protection across all major platforms
- Adaptive streaming protocols (HLS/DASH) with segment-level encryption
- Dynamic watermarking creating forensic accountability and psychological deterrence
- Access controls including domain restrictions, device limits, and time-based expiration
- Behavioral analytics detecting suspicious patterns and anomalous usage
For content creators, educational platforms, and enterprises distributing premium video content, implementing these protections isn’t optional—it’s essential for business survival. The investment in robust security infrastructure typically returns 5-10x through reduced piracy, increased conversions, and protected intellectual property.
Start by assessing your content value and threat landscape, then implement protection measures proportional to risk. For high-value content, partner with specialized video security platforms like Inkrypt Videos that provide turnkey solutions combining all protection layers with enterprise-grade performance and global CDN delivery.
FAQs
Use DRM (Digital Rights Management) to encrypt and control access keys.
Employ streaming protocols like HLS or DASH to stream in segments.
Add dynamic watermarking and disable right-click options.
Videos displayed in browsers can be recorded or captured.
Skilled users can use developer tools or screen recordings to save content.
Prevention methods mostly deter casual users, not hackers.
Implement multi-DRM with a license server to hide encryption keys.
Use tokenized, time-limited URLs for secure access.
Combine encryption, watermarking, and geo-blocking techniques.
They deliver video in small encrypted chunks instead of full files.
Streaming in segments makes it harder to capture a complete file easily.
Disabling right-click helps stop most casual download attempts.
It won’t stop users who access source code or use screen capture tools.
Watermarking deters unauthorized sharing by tracing leaks.
Invisible watermarks don’t affect viewing but can identify sources of leaks.
Use platform-specific privacy settings to restrict downloads and visibility.
Platforms cannot prevent screen recording but can limit direct downloads.
Use DRM services (e.g., Google Widevine, Apple FairPlay), secure streaming, and signed URL tokens.
Yes, determined hackers can circumvent protections; the goal is to deter the majority.
Terms of service and copyright notices help, but technical prevention is more effective.
Tokens expire quickly and prevent URL sharing, controlling who can access the video.
Yes, screen recording captures the playback, bypassing download restrictions. Watermarking can help trace these leaks.