Table of Contents
ToggleChoosing the right DRM software requires balancing three critical factors: security tiers (Google Widevine vs. Apple FairPlay), integration costs, and user experience. Whether you need an enterprise-grade solution for premium video or a lightweight tool for internal documents, the ‘best’ provider depends on your specific distribution model. This guide compares the top DRM platforms and outlines the essential criteria—from API flexibility to pricing models—to help you select the best value vendor for 2026.
Get a Custom DRM Cost Estimate
Key Takeaways
Modern DRM goes far beyond password protection—it uses AI, blockchain, and dynamic encryption to actively prevent piracy and misuse in real-time.
Choosing the right DRM means aligning with your specific content type (e.g., videos, AI models), user access needs, and compliance standards.
AI-ready DRM tools now support watermarking, license revocation, and behavioral analytics to track leaks and unauthorized usage.
Zero-trust frameworks and role-based access control (RBAC) are essential for balancing strong security with a smooth user experience.
Cloud-based DRM is ideal for remote teams and scalability, while on-premises options suit organizations with legacy systems or strict compliance needs.
A successful DRM strategy includes proactive key rotation, multi-device support, and transparent UX for both internal and external users.
Emerging threats like AI-generated piracy and brand impersonation demand dynamic, always-on monitoring and automation.
Why Modern DRM Software Is Essential for Safeguarding Digital Assets
In today’s digital landscape, sharing files externally can feel like navigating the Wild West—fraught with risks like digital piracy, unauthorized redistribution, and IP theft. Digital Rights Management (DRM) software acts as a critical shield, enabling businesses to securely share sensitive content (e.g., patents, creative assets) while retaining full control over usage permissions.
How DRM Works: From Basics to Advanced Security
DRM solutions range from simple file restrictions (like password-protected PDFs) to enterprise-grade systems with dynamic encryption, user authentication, and AI-driven access controls. Modern tools go beyond read-only settings, offering:
Real-time license management to revoke access remotely.
Dynamic watermarking to trace leaks.
Multi-device compliance for hybrid workforces.
The Evolution of DRM: Solving Legacy Challenges
Early DRM systems faced criticism for poor user experience, weak security (easily bypassed hacks), and complex setups. Today’s cloud-based DRM platforms prioritize:
Seamless integration with tools like Microsoft 365 or Google Workspace.
GDPR/CCPA compliance for global data privacy.
Cost-effective scalability, even for SMBs.
Choosing the Right DRM Software in 2025
Focus on solutions that align with your content type (e.g., video, software, documents), audience size, and compliance needs. Prioritize platforms offering:
AI-powered threat detection to block unauthorized sharing.
Detailed usage analytics for auditing.
Developer-friendly APIs for custom workflows.
What Is DRM?
A 2025 Guide to Digital Rights Management
Digital Rights Management (DRM) refers to technologies and systems that control access, usage, and distribution of digital content—from ebooks and music to sensitive corporate data. Unlike traditional ownership models, DRM shifts control (not legal ownership) to creators, allowing them to enforce rules like view-only access, device restrictions, or time-limited licenses.
Why DRM Matters in the Age of AI and Piracy
With the rise of AI-generated content, peer-to-peer (P2P) sharing, and torrent-based piracy, DRM has become a cornerstone of cybersecurity. It addresses critical challenges:
Preventing IP theft: Block unauthorized copying/redistribution of films, software, or patents.
Ensuring compliance: Meet GDPR, CCPA, and industry-specific regulations.
Safeguarding revenue: Protect subscriptions (e.g., streaming services) and digital product licensing.
How Modern DRM Works: Beyond Basic Encryption
Today’s DRM solutions leverage AI-powered watermarking, blockchain-based ownership tracking, and dynamic encryption to:
Restrict screen recording or screenshot tools.
Automatically revoke access for expired users.
Track leaks via geolocation or user-specific metadata.
How DRM Mechanisms Combat Digital Piracy in 2025
Digital content theft has evolved from casual downloads to AI-driven piracy networks and brand impersonation scams. While some steal intentionally (e.g., counterfeiters selling knockoffs), others unknowingly violate laws by using unlicensed images or outdated assets. Modern DRM tackles both scenarios through proactive content control and automated compliance audits.
Core DRM Strategies: Copy Protection + Permission Management
Copy Protection:
- Blocks right-click downloads, screenshots, or screen recording tools.
- Uses dynamic watermarking to trace leaked files (e.g., Netflix’s subscriber-specific marks).
Permission Management:
Grants granular access via DAM systems (e.g., Adobe Experience Manager).
Enforces zero-trust access controls by restricting IPs, geolocations, or user roles.
Why DRM Is Critical for Brand Integrity
Outdated assets—like expired logos or deprecated marketing materials—can damage brand trust if misused. DRM mitigates this with:
AI expiration triggers to auto-revoke access to old files.
Blockchain-based ownership logs for tamper-proof audits.
- Real-time compliance alerts for GDPR/CCPA violations.
How to Implement AI-Ready DRM in 2025: A Developer’s Blueprint
Deploying DRM in video platforms requires balancing security, scalability, and user experience. Here’s how to future-proof your workflow for AI-driven threats and multi-device ecosystems:
Phase 1: Pre-Implementation Audit
Assess Architecture:
Audit current tech stack for zero-trust compatibility (e.g., microservices, serverless setups).
Use tools like AWS Media Services or Microsoft Azure DRM to identify encryption gaps.
Select a Multi-DRM Provider:
Prioritize providers supporting Widevine (Android), FairPlay (iOS), and PlayReady (Windows).
Validate AI-powered threat detection features (e.g., watermarking for TikTok/YouTube leaks).
Phase 2: Integration & Encryption
1. SDK/API Setup
Use React Native SDKs (e.g., Video.js with Shaka Player) or low-code plugins for Moodle/WordPress.
For custom apps, leverage Google’s Cast SDK or Apple’s AVFoundation.
2. AI-Driven Content Encryption
Encrypt videos with AES-256 or MPEG-DASH CMAF for 4K/HDR streams.
Apply dynamic watermarking (user-specific or session-based) via tools like Nagra or Irdeto.
3. License Server Configuration
Deploy scalable license servers (e.g., AWS Elemental MediaLive) with tokenized access (JWT/OAuth 2.0).
Enable offline playback with time-bound licenses.
4. Cross-Platform Testing
Validate playback on Android TV, iOS Safari, and Smart TVs using BrowserStack.
Test DRM robustness against screen recorders and VPN bypass tools.
Phase 3: Launch & AI-Powered Monitoring
Deployment: Roll out DRM via CI/CD pipelines (e.g., GitHub Actions, Jenkins).
Real-Time Analytics: Use Google Analytics 4 or Pallyy to track:
Geographic piracy hotspots.
Device-specific playback failures.
Automated Alerts: Set up SOC dashboards (e.g., Splunk) to flag unauthorized redistribution.
2025 Best Practices for DRM Success
Multi-DRM Strategy: Cover Android, iOS, and OTT platforms with unified tools like Axinom.
Zero-Trust License Requests: Require MFA for high-value content access.
Proactive Key Rotation: Automate key updates using Hashicorp Vault or AWS KMS.
User Transparency: Explain DRM in FAQs (e.g., “Why can’t I screenshot this video?”).
Copy Protection in 2025:
Securing Digital Assets Against Unauthorized Use
Modern copy protection combines AI-driven encryption and behavioral analytics to block unauthorized access to digital content. Key techniques include:
Dynamic watermarking: Embed invisible, user-specific tags (e.g., Netflix’s subscriber-ID marks) to trace leaks.
Hardware-bound licensing: Restrict access to pre-approved devices (common in gaming DRM like Denuvo).
AI fingerprinting: Scan platforms for unauthorized copies using machine learning (e.g., YouTube’s Content ID).
Permission Management:
Balancing Security and Usability
Advanced permission systems leverage zero-trust frameworks to ensure that only verified users access sensitive data. Strategies include:
Multi-factor authentication (MFA): Require biometrics or hardware tokens for high-risk assets.
Geofencing: Block access outside approved regions (e.g., streaming services like Hulu).
Role-based access control (RBAC): Assign permissions via DAM platforms (e.g., Bynder or Widen).
How to Choose the Right DRM Software in 2025: 7 Key Considerations
Selecting a DRM platform requires aligning security needs with your content strategy. Here’s what to prioritize for AI-driven, compliance-focused environments:
1. Content Type & Complexity
Sensitive Documents: Protect patents (PDFs), financial models (Excel), or 4K video with multi-format DRM that supports AES-256 encryption.
AI/ML Models: Opt for solutions with runtime protection (e.g., NVIDIA DGX) to secure proprietary algorithms.
Avoid free tools limited to basic file types—scalability matters.
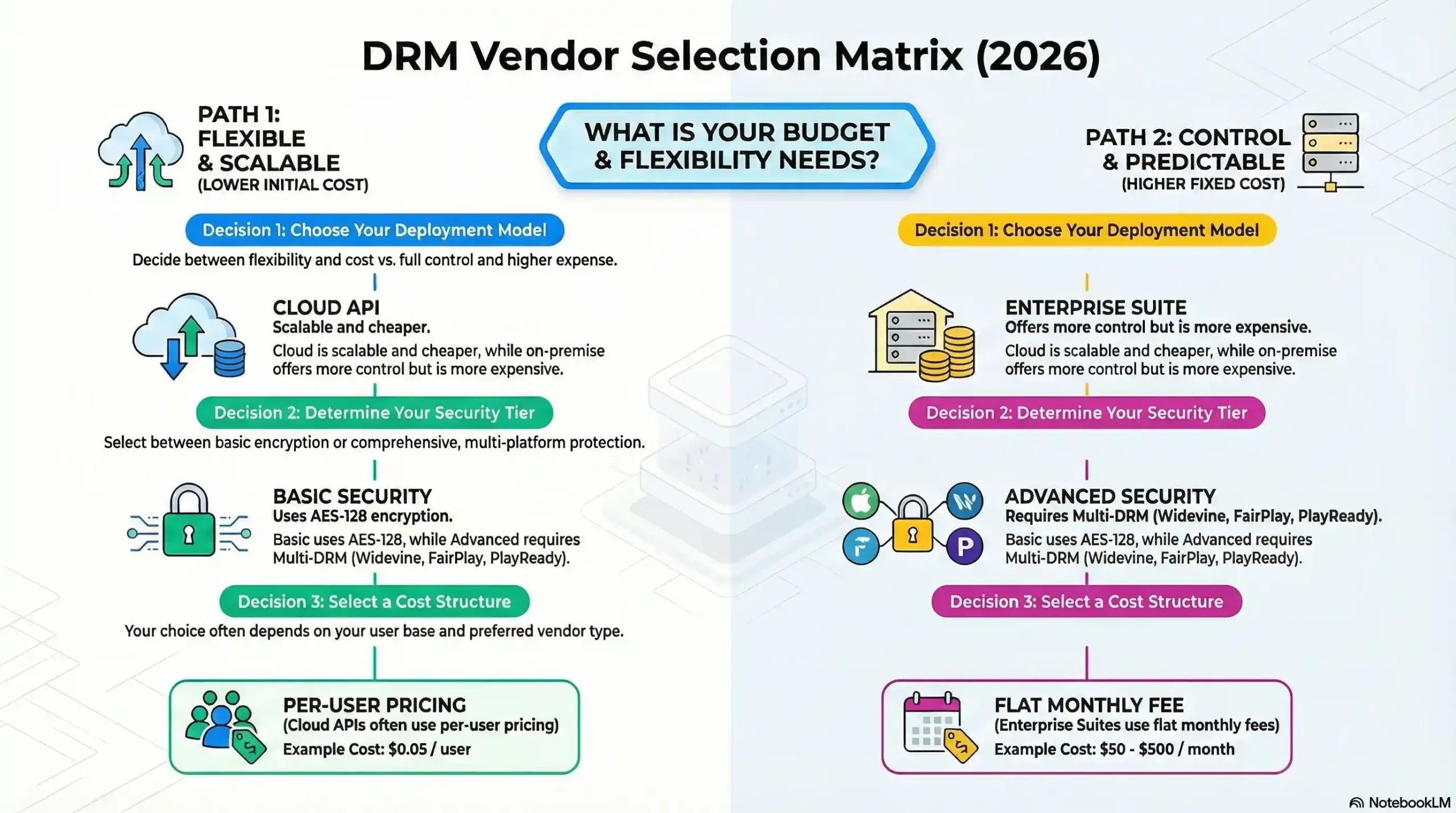
2. Security Tier Requirements
Basic: Use traditional DRM for read-only PDFs with password controls.
Advanced: Deploy hardware-backed DRM (e.g., Apple FairPlay) for streaming or GDPR/CCPA-compliant systems for sensitive data.
3. Legal & Analytics Capabilities
Modern DRM platforms like Microsoft Azure Rights Management offer:
Automated NDAs: Force users to accept terms before accessing files.
Behavioral Analytics: Track logins, downloads, and geographic access patterns.
Audit Trails: Generate compliance reports for regulators (e.g., HIPAA, SOX).
Audience-Centric DRM: Tailoring Security to User Needs in 2025
Choosing the right DRM hinges on who accesses your content and how they interact with it.
1. Define Your Audience & Access Levels
Internal Teams: Use on-premises DRM (e.g., Microsoft SharePoint) with zero-trust access for employees. Integrates seamlessly with existing tools like Slack or Teams.
External Stakeholders: Opt for cloud-based DRM (e.g., Citrix ShareFile) with cross-platform compatibility for investors or clients. Supports secure mobile access without VPNs.
B2C Sales: Deploy lightweight DRM for eBooks or courses, offering one-click access via email links.
2. Prioritize Frictionless User Experience (UX)
Internal Users: Automate permissions via Active Directory integration to eliminate login hassles.
External Users: Ensure browser-based viewing (no plugins/downloads) for files. For example, Adobe’s DRM lets users open protected PDFs directly in Chrome.
Compliance: Embed clickwrap agreements (like NDAs) during file access to meet legal standards.
3. Audit End-User IT Constraints
Corporate Networks: Avoid solutions requiring admin rights for installs—IT teams often block unauthorized software.
BYOD (Bring Your Device): Use HTML5 viewers or progressive web apps (PWAs) for hassle-free access on personal devices.
- Legacy Systems: Test DRM compatibility with older OS versions (e.g., Windows 10) if stakeholders lack updated hardware.
Cloud vs On-Premises DRM: Cost, Control, and Compliance in 2025
Choosing between cloud and on-premises DRM hinges on IT infrastructure maturity, compliance needs, and long-term scalability.
1. Cloud-Based DRM (SaaS Models)
Pros:
Zero Maintenance: Providers like AWS CloudHSM or Microsoft Azure handle encryption, updates, and uptime.
Global Access: Securely share files across regions without VPNs (ideal for remote teams).
Pay-as-You-Go: Scalable pricing aligns with usage (e.g., $0.05/GB for encrypted storage).
Cons:
Limited customization for niche compliance (e.g., defense contractors requiring air-gapped systems).
2. On-Premises DRM (Self-Hosted)
Pros:
Full Control: Customize security protocols for legacy systems (e.g., healthcare with HIPAA mandates).
No Recurring Fees: Avoid SaaS subscription costs.
Cons:
High TCO (Total Cost of Ownership): Requires dedicated IT staff, hardware upgrades, and energy costs (e.g., $15k+/year for mid-sized firms).
Budgeting for 2025: Balancing Security and ROI
Free Tools: Risky for sensitive IP—lack AI threat detection or GDPR compliance.
Enterprise Solutions: Platforms like VeraCrypt Enterprise offer tiered plans ($50–$500/month) with audit trails and multi-device support.
Hybrid Models: Combine cloud flexibility with on-prem control (e.g., store data locally, and manage keys via AWS KMS).
Future-Proof Your Content Security: Final Steps for 2025
Adopting a cloud-first DRM strategy offers rapid deployment (under 24 hours) and predictable costs—critical for businesses scaling AI-driven content or global teams. Platforms like AWS CloudHSM or Adobe Experience Cloud provide enterprise-grade security without upfront hardware investments.
Why Choose Modern DRM in 2025?
Zero-Trust Compliance: Align with GDPR, CCPA, and ISO 27001 using automated access controls.
AI-Powered Analytics: Track leaks in real-time with tools like Pex or VeraCrypt.
Cost Transparency: Cloud DRM averages $0.10–$1.00/user/month, vs. $10k+ for on-prem setups.
Partner with DRM Experts
For specialized needs (e.g., 4K video protection or AI model security), collaborate with certified providers like Inkrypt Videos, whose FIPS 140-2 validated encryption secures clients like Netflix and Disney+. Their end-to-end services include:
Custom SDKs for app integrations.
Multi-DRM support (Widevine, PlayReady, FairPlay).
- 24/7 SOC monitoring to counter piracy networks.
Secure Your Digital Future Today
Don’t wait for a breach to act. Upgrade to AI-powered DRM solutions and protect your content, IP, and brand integrity in a rapidly evolving digital world.
FAQs
What is DRM software and why do I need it for my video content?
DRM software encrypts and controls access to your videos, preventing unauthorized use and piracy to protect your content and revenue
How do I choose the right DRM software for my video platform?
Consider device compatibility, security features like encryption and watermarking, user experience, and integration ease with your existing system
Can DRM affect the viewer’s streaming experience?
Yes, DRM can cause playback delays or quality limits on some devices, so choose DRM that balances security with smooth user experience
What security features should I look for in DRM software?
Look for encryption, license key protection, watermarking, geo-restrictions, and multi-DRM support for broad device compatibility
How does DRM handle different devices and browsers?
DRM uses multiple encryption schemas like Widevine and Fairplay to support various devices and browsers, ensuring secure playback across platforms
Is DRM unpopular with customers and does it reduce sales?
If implemented with a seamless user experience and clear subscription options, DRM does not deter customers and can increase revenue
Can DRM prevent video downloads and unauthorized sharing?
Yes, DRM encrypts videos and controls playback, blocking downloads and unauthorized sharing via plugins or software
How does DRM encryption protect video content?
DRM encrypts videos with unique keys, allowing only authorized users to decrypt and view the content securely
What are the most popular DRM providers for video?
Top DRM providers include Google Widevine, Apple Fairplay, and Microsoft PlayReady, often combined via multi-DRM services
Can I restrict video access by location with DRM?
Yes, many DRM solutions offer geo-restrictions to allow or block video playback based on the viewer’s geographic location
How does watermarking enhance DRM protection?
Watermarking embeds invisible marks in videos to trace leaks back to the source, deterring piracy and unauthorized sharing
What should I avoid when implementing DRM for my videos?
Accordion ConteAvoid complex DRM setups that cause playback failures or frustrate users; aim for a balance of security and smooth viewingnt


